Save to My DOJO
If you’re an MSP, there’s a big change coming in how you manage your client’s Office 365 tenants and Microsoft 365 tenants. Microsoft 365 Lighthouse is a modern way to manage multiple clients’ users and devices in a single pane of glass. This article will show you how to set up the preview, how to make sure your clients appear, and how to manage settings and policies across all of them.
Note that Microsoft 365 Lighthouse is a different service than Azure Lighthouse, which lets an MSP manage resources in their client’s Azure subscriptions securely. It makes sense to name the services similarly since the concept of a “service provider managing a client’s cloud service” is the same, but it’s bound to cause some confusion. We’ve looked at Azure Lighthouse here:
Just as Azure Lighthouse has been a game-changer for the business model of MSPs, Microsoft 365 Lighthouse will be a turning point for MSPs as well, with the difference that every MSP I know has all their clients on Office / Microsoft 365, while not everyone uses Azure.
Signing up for the preview
Before we get to the requirements to use Microsoft 365 Lighthouse, let’s get it activated in your MSPs M365 tenant. It’s a straightforward process. But it can take up to 24 hours; in my case, it only took a few hours.
Sign into your tenant at admin.microsoft.com, go to Billing > Purchase services > Other services, search for Microsoft 365 Lighthouse public preview, and buy a single license for $0. There’s no cost for Microsoft 365 Lighthouse during the preview or after General Availability, just like Azure Lighthouse.

Purchase Lighthouse public preview
After some time, you’ll receive an email to let you know that your tenant has been enabled for the preview.

Microsoft 365 Lighthouse enabled
Microsoft 365 Lighthouse requirements
There are a few things that need to be in place for you to take advantage of Microsoft 365 Lighthouse.
First, your MSP must be enrolled in the Cloud Solution Provider (CSP) program as an Indirect Reseller or Direct Bill partner.
Secondly, each client must provide Delegated Admin Privileges (DAP) to your MSP.
Thirdly, at this time, each client must have at least one Microsoft 365 Business Premium license and fewer than 500 licensed users. I suspect some of these limitations will be lifted after General Availability (GA). I’m sure many businesses larger than 500 users are already using an MSP to manage their Office 365 tenant, just as many smaller businesses rely on the advanced security features in Microsoft 365 E5, for instance.
Still, their MSP would like to manage them using Lighthouse. With no inside information, I suspect Microsoft is focusing on this market segment to start with because it’s the one many MSPs focus on, and converging on Business Premium only also makes sense as it gives a common set of features to manage using Lighthouse.
Fourth, if you want to manage tenant devices, they must be enrolled in Microsoft Endpoint Manager (MEM).
Fifth, for user account data to appear in reports, the client’s tenants must have Azure Active Directory Premium P1, which is included in Microsoft 365 Business Premium.
Sixth, to see devices on the threat management pages, they must be running Microsoft Defender Antivirus (built into Windows). This one could be a bit tricky; many MSPs rely on their favorite AV tool and may not want to move to the built-in solution, but (if you’re stuck in the past) know that Defender AV is quite capable these days and is also a stepping stone to the excellent Microsoft Defender for Endpoint (MDE).
The last three on the list won’t stop you from using Microsoft 365 Lighthouse but will limit the functionality as mentioned.
In summary:
- Enroll in the Cloud Solution Provider program
- Invite each client to Delegated Admin Privileges
- Ensure the clients have at least one Microsoft 365 Business Premium license
- Enroll devices in Microsoft Endpoint Manager
- Make sure the clients have Azure Active Directory Premium P1
- Enable Defender Antivirus
Enrolling in the Cloud Solutions Provider program
I suspect most Microsoft-based MSPs have already completed this step, and my MSP took this step a few years ago, so I don’t have screenshots to show you the process, but here’s the official documentation.
Your primary choice is between being an indirect reseller, where you buy Azure / Microsoft 365 and on-premises licensing through CSP via a distributor, or being a direct bill partner. The latter requires you to provide the first level of support for your clients, fully manage customer billing and provisioning, and generate at least 300,000 USD revenue in cloud sales in a 12-month period. Here’s the page to get started as an indirect reseller.
Once enrolled, the CSP area in the Partner Center lights up, and you can manage clients here.

CSP in Partner Center
Invite a client to Delegated Admin Privileges
I suspect there’s a bit of dirty laundry in most MSPs’ cupboards (including mine) where they don’t have delegated access to their client’s tenants but instead have Global Admin accounts to log in directly to each tenant to do any administration. If that’s the case, please ensure that those Admin accounts have MFA enabled.
To use Microsoft 365 Lighthouse, you need to set up your MSP with delegated admin rights to each tenant. Start by clicking the link “Request a reseller relationship” in the CSP portal. Pick your indirect provider, make sure “Include delegated administration privileges” is selected, and edit the email before sending it to your client. Note that the recipient must be a Global Administrator in the tenant to be able to action it.

Request a reseller relationship in the CSP partner portal
When a global admin for the tenant clicks the link in the email, they’re greeted with this screen and simply click the Authorize button.

Authorize client for Delegated Admin Privileges
They should now show up under customers in your CSP portal, in my case, this was nearly instantaneous.
Exploring the Microsoft 365 Lighthouse portal
Logging on to the Home page
Go to https://lighthouse.microsoft.com and sign in with an account in your MSP tenant with Global Admin credentials and MFA enabled. If the account doesn’t have MFA enabled, you’ll need to enable it before being able to sign in.
In case you find this burdensome, understand that you’re effectively accessing all your tenants in one place using Lighthouse, so enforcing MFA is a must. I would also suggest that access to Lighthouse should be limited to approved, locked-down admin workstations, something you can do using Conditional Access in AAD.
According to Microsoft, it can take up to 48 hours before client data starts showing up in the portal. Again, in my experience, it took less than two hours.

Home in the Microsoft 365 Lighthouse Portal
On the Home page is an overview of my clients, with tiles for threats (Defender Antivirus), devices with it installed, risky users, and device compliance. You can filter this view with the Tenants button in the top left.
User account pages
When I drill into the Risky user’s tile, I’m taken to the Users part of Lighthouse, where four tabs show accounts that have been flagged as risky and their current status (At risk or remediated). Clicking View risk detections for an individual account takes me to the AAD portal for that tenant to investigate the risk.
The Multi-Factor Authentication tab shows the tenant’s status for MFA enablement and users not registered for MFA. In contrast, the Password reset tab shows the tenants’ state and accounts for Self-service password reset (SSPR). I can also search across all usernames, and when I find a particular user, I can reset their password or block sign-in. Particularly, password reset is a very common action for MSP helpdesk staff. Instead of signing into a client’s tenant, finding the user, and then resetting their password, you can do it here for any user.
 Risky users blade
Risky users blade
Antivirus and Threats
Clicking either the Threat or Antivirus tile takes me to the Threat management area, where an overview tab shows me threats (active / mitigated / resolved), devices missing Defender AV, and devices overdue for scans. The Threats tab shows a list of active, mitigated, resolved, and allowed threats, whereas the Antivirus protection tab shows me a list of devices, their state, if the AV is up to date, real-time protection state, and if any scheduled quick or full scans are due.
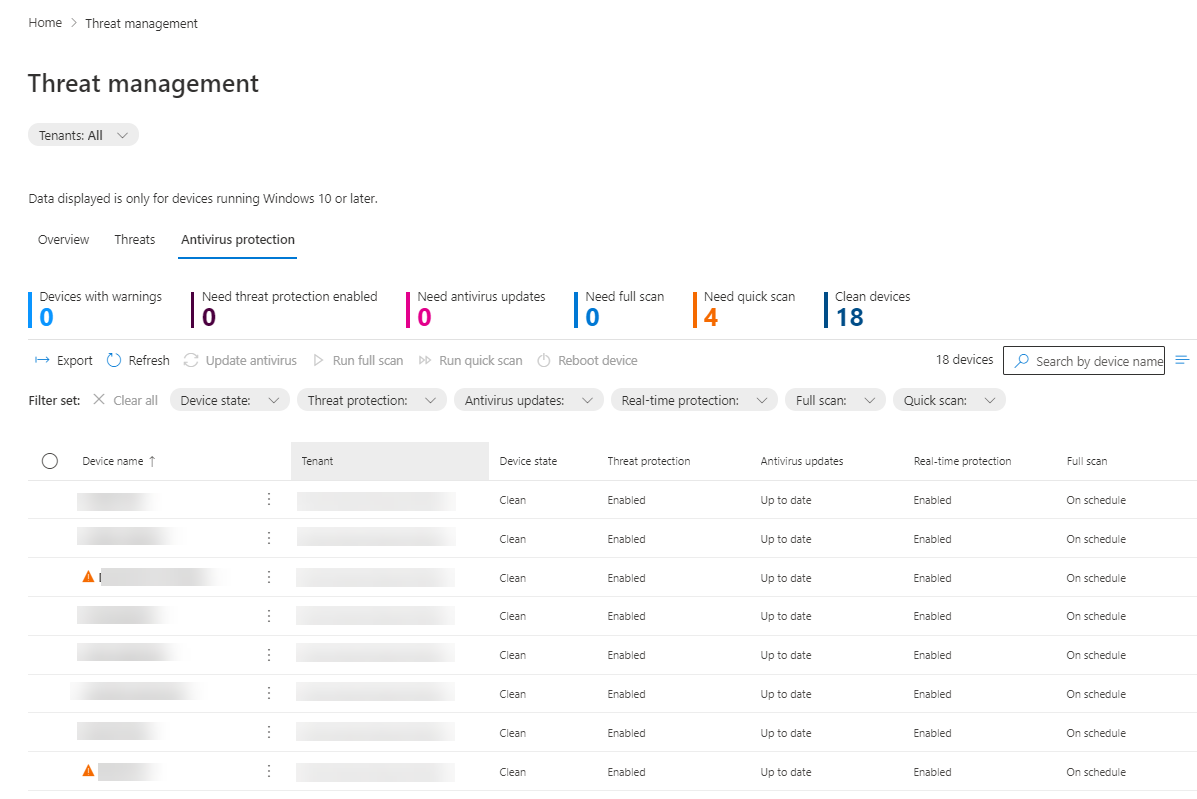
Antivirus status across each device
The orange warnings in the screenshot show quick scans that are overdue. Clicking on an individual device brings up its details, plus options to run a quick or full scan, update the signatures and reboot the device.

Device details in Antivirus view
Note that you can also multi-select several devices and run scans on all of them or even reboot all of them in one fell swoop. You can also filter the view of the devices based on device state, threat protection, update status, and any overdue scans.
Devices & Tenants
The Device area has four tabs: Overview shows devices managed by compliance policies in MEM, whereas the Devices tab shows the compliance status for each device with the ability to filter the view based on whether the device is corporate or personal, the OS it is running, and its status.
The Policies tab syncs from MEM, whereas the Settings tab shows non-compliant settings across tenants. In this area of Lighthouse, I noticed that the data on some tabs were missing, possibly due to the 48 hours not having passed after adding the tenant. You can also click an individual device to see details and click a link there to see it in the full Endpoint Manager console.

Device compliance with MEM policies view
The Tenants view shows tenants, including ones ineligible for Lighthouse (missing license for Microsoft 365 Business Premium, for instance) or ones that don’t yet have Delegated Administrative privilege. You can create and assign tags to different tenants as a way to organize them.
Security and Baselines
There are two specific role-based access control (RBAC) roles associated with the Microsoft 365 Lighthouse: Admin Agent and Helpdesk Agent. The former has permission to change most settings, whereas the latter can view everything but only reset passwords, block sign-ins, and update customer contact / website details.
Microsoft recommends using Privileged Identity Management (PIM), a feature in AAD Premium P2 (in the partner tenant) to enforce the principle of least privilege so that a Helpdesk Agent can be eligible to be an Admin Agent but must go through a PIM workflow, which can include entering a service ticket, being approved by a supervisor and perform an MFA to elevate to that permission, for a restricted time of a few hours.
Security baselines are a key feature in Microsoft 365 Lighthouse. Today, you can’t edit them; there are six default baselines:
- Require MFA for admins (CA report only policy)
- Require MFA for end users (CA report only policy)
- Block legacy authentication (CA report only policy)
- Enroll devices in MEM & Azure AD Join
- Antivirus policy – a Device Configuration profile
- Windows 10 Compliance policy
In the baseline area, I can see the Default baseline and apply it to groups of clients. Note that the three Conditional Access policies are reported only and thus won’t actually enforce the setting. Just give you reports on where it would have been applied. This is a good way to get a grip on the state of MFA and legacy authentication usage across your tenants but in today’s security-challenged business landscape, it’s vital to move to enforcing MFA and disabling the legacy protocols as soon as possible.
There are two other areas in Microsoft 365 Lighthouse: Windows 365 gives a view of any Cloud PCs in your client’s tenants and their network connections to on-premises. I don’t have any clients using Windows 365 yet, but it makes great sense to surface this information in Lighthouse.
The final area is Service health, which shows advisories and incidents across Teams / Microsoft 365 / Exchange Online and another 20 services. It’s the same view as in the Microsoft 365 Admin Centre, but having it handy in this portal makes sense.
Conclusion
This is a public preview, and both the functionality and requirements are a bit limited, but I suspect this will change as feedback comes to Microsoft, particularly now that it’s in public preview. There’s a specific UserVoice for Microsoft 365 Lighthouse – join here.
I think Microsoft 365 Lighthouse will be a game-changer for MSPs. It’s a shift in how you manage your clients’ digital estates at scale, and I suspect that it’ll find fans in both large and small MSPs. At this stage, I have questions about the shared MSP model, which works in Azure Lighthouse, where you can have one MSP managing your backups and IaaS VMs and another MSP handling your databases. Today, that’s not supported in Microsoft 365 Lighthouse.
Another concern is the overlap with third-party MSP management tools, and my initial take is that I’m far more likely to trust Microsoft to get security right rather than the RMM software vendors of today (especially given recent news), plus a first-party provided tool is always preferable to me personally. Full disclosure – I don’t use an MSP tool in my business, but I do rely on N-Able Take Control for remote access to devices.
Microsoft 365 Lighthouse isn’t replacing a Remote Monitoring and Management (RMM) tool today. Once the functionality is expanded, I can see this being one of the main tools in your MSP toolbox.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!







