Save to My DOJO
One of the most common types of cyberattacks is one where cybercriminals seek to compromise the victim’s web credentials. Using email-based phishing attacks and increasingly convincing social engineering techniques, victims are tricked into providing their user ID and password for a wide range of cloud-based platforms and applications.
According to our 2023 Cybersecurity Report, phishing remains the most common type of email attack, constituting 39.6% of all detected threats. What makes online credentials so appealing to cybercriminals is the access these credentials provide to online banking, Office 365, Azure apps via Azure Active Directory, financial applications, customer data, and more. Gaining access to these kinds of applications and data can be detrimental to SMBs – potentially even causing them to shut their doors.
So, how can you as an MSP help protect your customers from this kind of cyberattack?
The answer lies in Multi-Factor Authentication (MFA).
Now let’s get onto some MFA basics and then talk about how you can incorporate this security control into your service offerings.
What is Multi-Factor Authentication?
Multi-Factor Authentication (MFA) is a security method that uses multiple identifying “factors” to verify a user’s identity instead of relying on the traditional username and password. MFA requires additional factors to identify and authenticate the user. These factors include:
- Text messages to the user’s smartphone
- Sending codes to an alternate email address
- Asking additional security questions
- Using secondary authentication to trusted 3rd party sources
- Biometrics (such as fingerprint or retina scan)
- Facial recognition
- Security hardware token device
- Security token app on a user’s smartphone
- Certificates
Additionally, depending on the MFA solution being used, details about when and from where the authentication request can come into play, including location, day/time, IP address, requesting device’s MAC address, etc.
All of these factors – in one form or another – fall into one of three generally accepted authentication factors:
- Something you know – This can be information relevant to authentication that the user themselves knows already, such as passwords, answers to security questions, etc.
- Something you have – These are generally represented by physical items the user possesses, such as a smartphone, security token, or RFID badge.
- Something you are – This is where biometrics and facial recognition come into play. This factor uses any part of your personality that can help uniquely identify you.
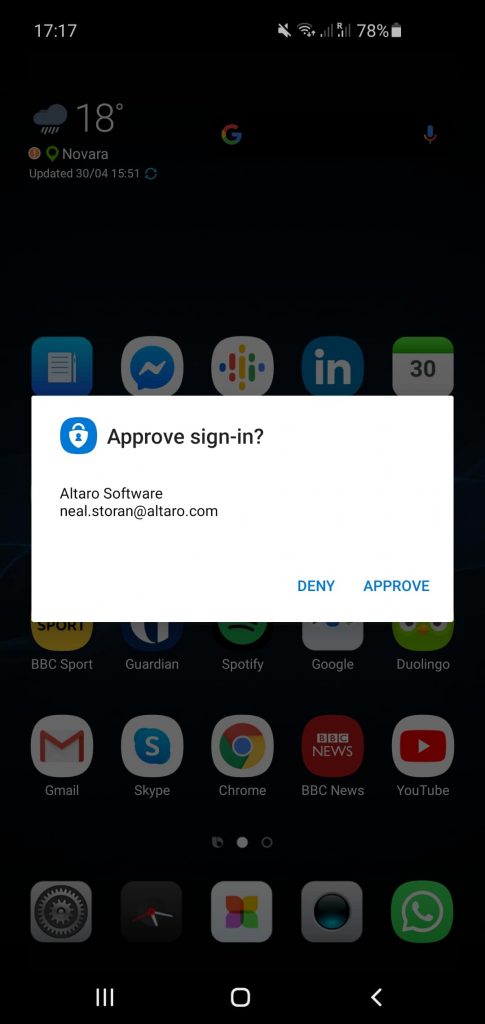
Office 365 2 Factor Authentication Mobile Sign In
How Does MFA Work?
First off, notice we’re discussing multi-factor authentication. The focus here is for you to use multiple factors with your customers. Why? Because each of these factors on their own can be (and in many cases, have been) hacked or spoofed. Mobile devices have had their SIMs swapped for an attacker-controlled device, passwords can be cracked, and even fingerprints have been shown to be spoofable using 3D printing.
With MFA, the user authenticates by providing a number of factors – how many depend on the level of security needed, the individual’s role within the organization, etc. In general, the user first provides their usual username and password. Once provided, they are then presented with one or more additional challenges where the implemented factors mentioned above need to be satisfied.
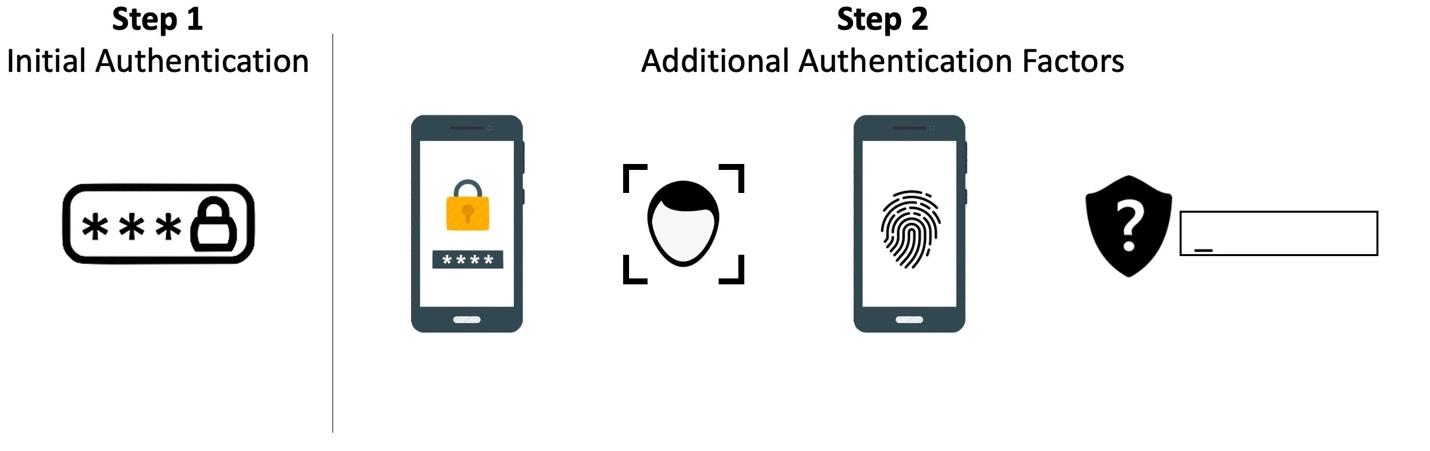
Multi-Factor Authentication Steps
Where Do You Find MFA?
There are dozens and dozens of software vendors offering MFA. In many cases, it’s offered as part of a larger Identity and Access Management solution – which may be too complex for simply implementing MFA for your SMB customers. Microsoft offers Azure Multi-Factor Authentication to secure access to Azure Active Directory, Office 365, Azure-based VMs, applications, and data, as well as to be a trusted authority for third-party cloud applications and platforms. This service is simple enough to scale down to an SMB’s needs. And as mentioned, there are a number of vendors offering MFA solutions that are simple and cost-effective enough for an MSP.
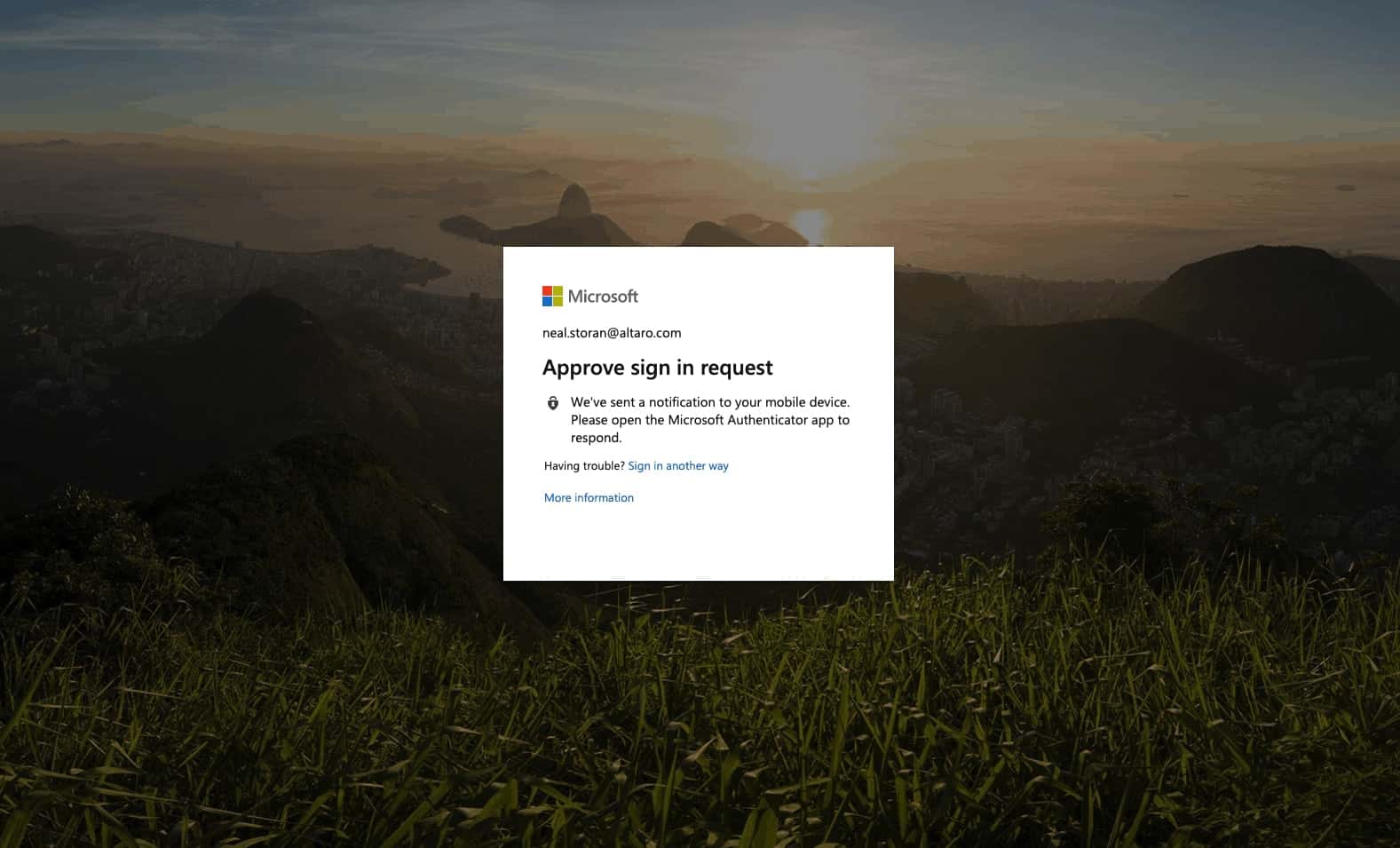
Office 365 2 Factor Authentication Desktop Sign In
Why is MFA No Longer an Option for MSPs?
For MSPs, MFA offers the chance to drastically enhance security and protect your customers. To deepen it, here are 5 reasons why MFA is no longer optional but necessary for MSPs.
- Prevent Cyber Threats
As cyberattacks grow in sophistication, no customer is immune to the risks of data breaches, ransomware, or phishing. MFA serves as a critical defense layer, rendering stolen credentials useless without the additional authentication factors, thereby protecting against unauthorized data access and system breaches.
- Compliance and Industry Standards
The regulatory landscape is increasingly stringent, with numerous industries mandating MFA to safeguard sensitive data. For MSPs, non-adherence is not an option; failure to implement MFA can lead to severe penalties, legal ramifications, and reputational harm. It’s essential for meeting both compliance obligations and customer expectations.
- Stringent Access Protocols
With the proliferation of remote work and cloud-based platforms, robust access controls are paramount. MFA ensures that only verified users can access critical applications and data, providing a significant barrier against unauthorized access and potential internal or external breaches.
- Mitigating Fraud and Identity Theft Risks
The threat of identity theft and fraud is ever-present in the digital age. Implementing MFA introduces a formidable challenge for cybercriminals attempting to impersonate users or commit fraud, thus safeguarding business operations and sensitive information from such illicit activities.
- Building Trust and Safeguarding Reputation
In a world increasingly conscious of cybersecurity, customers expect and demand stringent protection of their data. By implementing MFA, MSPs demonstrate a commitment to security, fostering trust, and reinforcing their reputation as a protector of customer interests and data integrity.
How to Go about Offering MFA to Your Customers
MSPs have several options to go about this. The first is to simply absorb the cost of setting up MFA and offer it at no charge. Microsoft Azure MFA has a free version that is a very viable option. If you are offering either Managed Office 365 services or Managed Security services, I’d suggest bundling it in as part of those services. For those SMB customers that are on the larger side and need MFA integration with single-sign-on access to multiple cloud applications, you’ll want to look at vendors like Okta, who focus on integrating their MFA with thousands of existing cloud products and services.
It’s Time to Secure Your Customer With MFA
Multi-Factor Authentication needs to be an embedded part of your service offerings intent on keeping your customer’s applications and data safe from cyberattacks intent on gaining access. By implementing MFA in your customer’s environments, you’ll help to minimize the risk of successful cyberattacks focused on credentialed access.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









