Save to My DOJO
In this blog post, we’ll be talking about Azure Arc and how VMware admins can leverage it for management purposes.
At Microsoft Ignite 2019, Microsoft announced the public preview of Azure Arc. This new service is the management Godzilla that may very well set Azure apart from other cloud providers. It extends the feature set of Azure Resource Manager to servers and Kubernetes clusters and provides a centralized management platform for these endpoints whether they reside on-premise or even in other public clouds like AWS and GPC.
As of right now, Azure Policy Guest Configuration and Log Analytics are the only services available with Azure Arc managed servers. There is also no pricing scheme set up at the moment for this service while it is in preview. While this new and shiny service is in its infant stage, Azure Arc can be a fantastic way for managing all resources with a single panel of glass especially for VMware Administrators that are running a hybrid cloud infrastructure. In order to onboard servers into Azure Arc, an agent must be installed on each server. Below are the steps for getting started.
Requirements and Limitations
Azure Arc is currently compatible with the following server OSes:
Windows Server 2012 or newer
Ubuntu 16.04 and 18.04
By default, you can only have 800 Servers per Resource Group. So keep this in mind when planning. Azure Arc requires an outbound connection to the Azure Arc services and also works with an HTTP proxy, so for any networking configurations be sure to check out their network configuration guide.
Installing the Azure Arc Providers
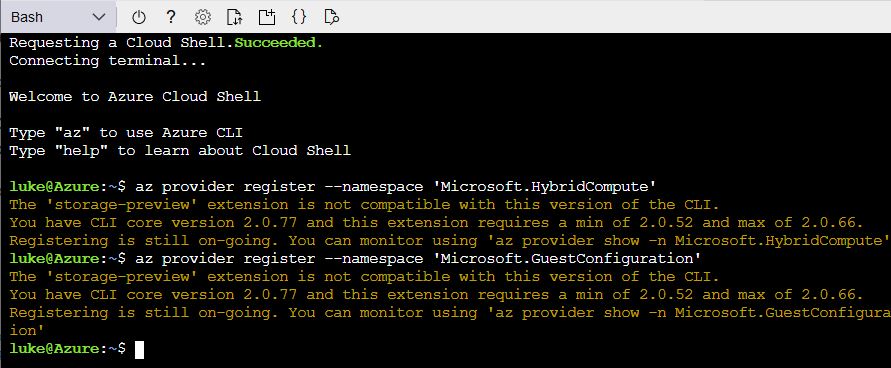
Before we can start using Azure Arc, we need to register the providers. The easiest way to do this is to open up a CloudShell environment or login to Azure CLI and type in the following commands:
az provider register --namespace 'Microsoft.HybridCompute' az provider register --namespace 'Microsoft.GuestConfiguration'
Now that we have both required providers registered we are ready to connect a Windows and Linux server in our VMware environment to the Azure Portal by deploying the agent to them.
Deploying Agent On-Premise
The quickest way to get some agents connected is with PowerCLI. To do this we will need to create a Service Principle which will be used to authenticate with our Azure Subscription and onboard our VMs. The fastest way to create a SP is by pasting the following command into Azure CLI. We will be assigning our SP the “Azure Connected Machine Onboarding” role. This is a role that Microsoft has made specifically for onboarding VM’s to Azure Arc, it has a very limited scope of permissions:
az ad sp create-for-rbac --name sp-lukelab-azurearc --role "Azure Connected Machine Onboarding"
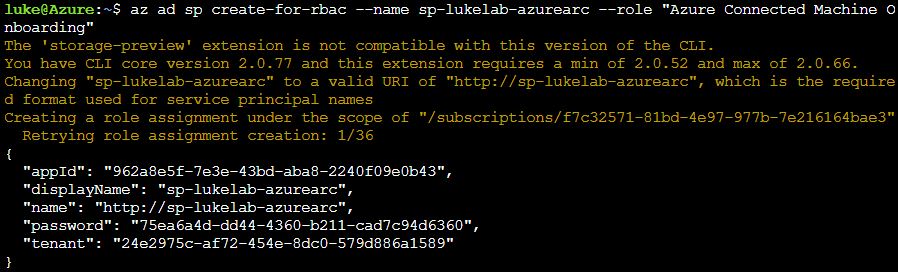
Take note of the AppID and Password. We will need to feed these into our PowerCLI script. If you don’t have PowerCLI installed on your machine, run the following command:
Install-Module VMware.PowerCLI -Force
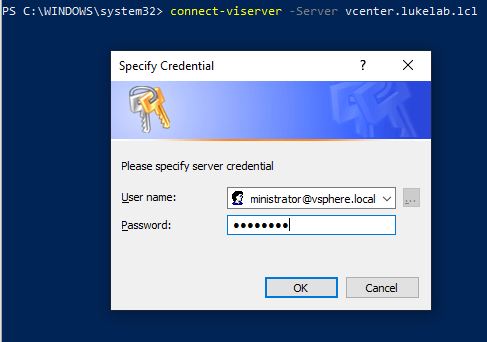
Then we need to connect to our VCenter environment with the following syntax. In the example, my VCenter server’s name is “vcenter.lukelab.lcl”. Input the credentials to VCenter to successfully connect:
Connect-VIServer -Server vcenter.lukelab.lcl
Now let’s install an agent on Ubuntu and Windows. Microsoft provided a script for each OS version, we will use PowerCLI to invoke the script on each OS.
Installing on Windows
Fill in the service principle, resource group, subscription, and tenant ID with your own details:
$installscript = @' # Download the package Invoke-WebRequest -Uri https://aka.ms/AzureConnectedMachineAgent -OutFile AzureConnectedMachineAgent.msi # Install the package msiexec /i AzureConnectedMachineAgent.msi /l*v installationlog.txt /qn | Out-String & "$env:ProgramFiles\AzureConnectedMachineAgent\azcmagent.exe" connect ` --service-principal-id "962a8e5f-7e3e-43bd-aba8-22sdfs234b43" ` --service-principal-secret "O31FafVA:mL_=zZoLo[JeMV8vLXrjWF3" ` --resource-group "rg-LukeLab-OnPremise" ` --tenant-id "24e2975c-af72-454e-8dc0-572345151" ` --location "WestUS2" ` --subscription-id "f7c32571-81bd-4e97-977b-7e2234323" '@ Invoke-VMScript -vm web1 -scripttype powershell -scripttext $installscript -GuestCredential (get-credential)
Paste the script into the PowerShell window that is already connected to VCenter through PowerCLI:
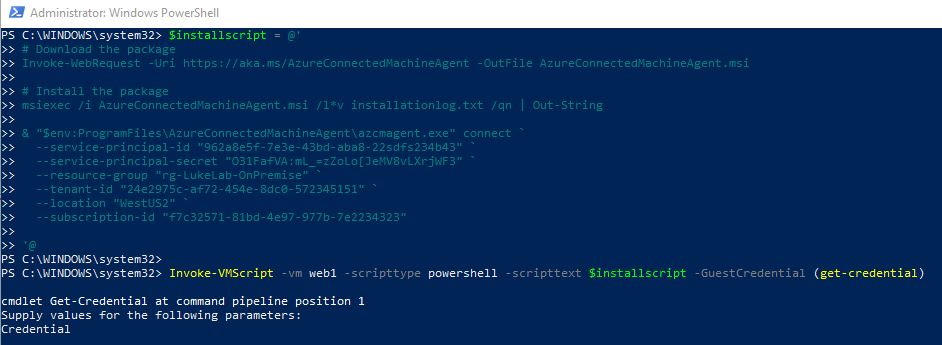
Now the script will run ad it will take a few minutes to install and show up in the portal.
Installing on Ubuntu
Just like with our Windows script, fill in the service principle, resource group, subscription, and tenant ID with your own details:
$installscriptlinux = @"
# Download the installation package
wget https://aka.ms/azcmagent -O ~/Install_linux_azcmagent.sh
# Install the connected machine agent. Omit the '--proxy "{proxy-url}"' parameters if proxy is not needed
bash ~/Install_linux_azcmagent.sh
azcmagent connect \
--service-principal-id "962a8e5f-7e3e-43bd-aba8-22sdfs234b43" \
--service-principal-secret "O31FafVA:mL_=zZoLo[JeMV8vLXrjWF3" \
--resource-group "rg-LukeLab-OnPremise" \
--tenant-id "24e2975c-af72-454e-8dc0-572345151" \
--location "WestUS2" \
--subscription-id "f7c32571-81bd-4e97-977b-7e2234323"
"@
Invoke-VMScript -vm web4 -scripttype bash -scripttext $installscriptlinux -GuestCredential (get-credential)
Then we invoke it with Invoke-VMScript:
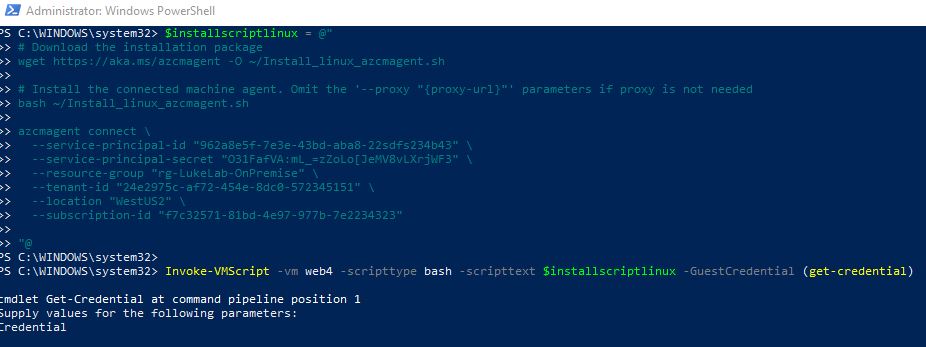
It will take a few minutes to install. Then the server will appear in the portal.
Managing Servers in the Azure Arc Portal
When we check the portal we can see both our Windows and Linux servers that reside on-premise are now added into Azure. We can now use Guest Configuration and Log Analytics with them. Let’s assign a policy to Web1:
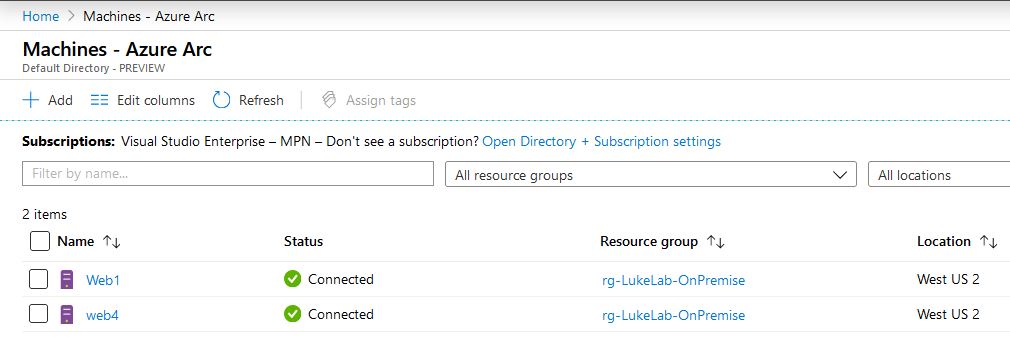
We select Web1 and choose “Assign Policy”:
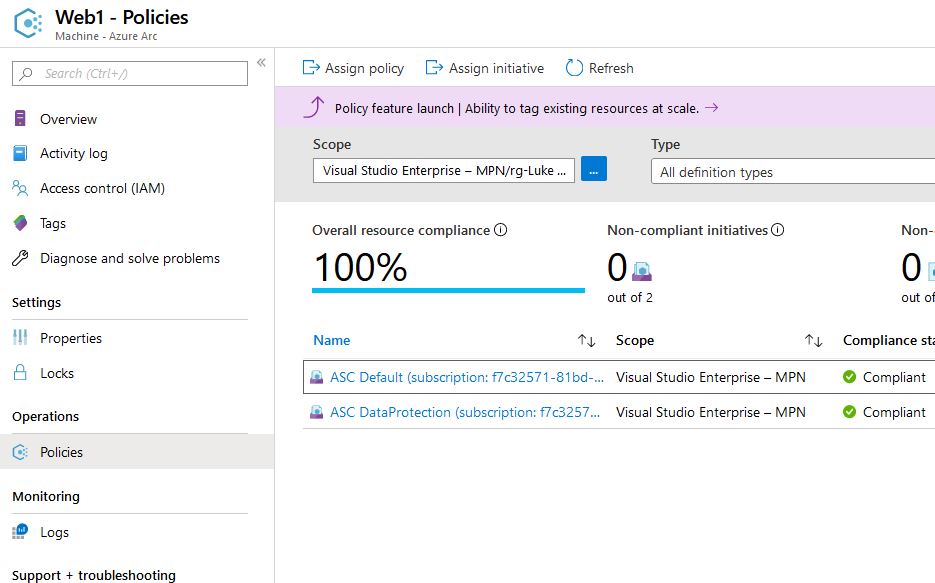
Select the resource group for the scope and we will select the policy definition “Configure time zone on Windows machines” this is currently the only configuration policy that can be enforced on guest VMs. More and more will be added in the future, but Microsoft wanted to start with something nonintrusive at first, like setting the time:
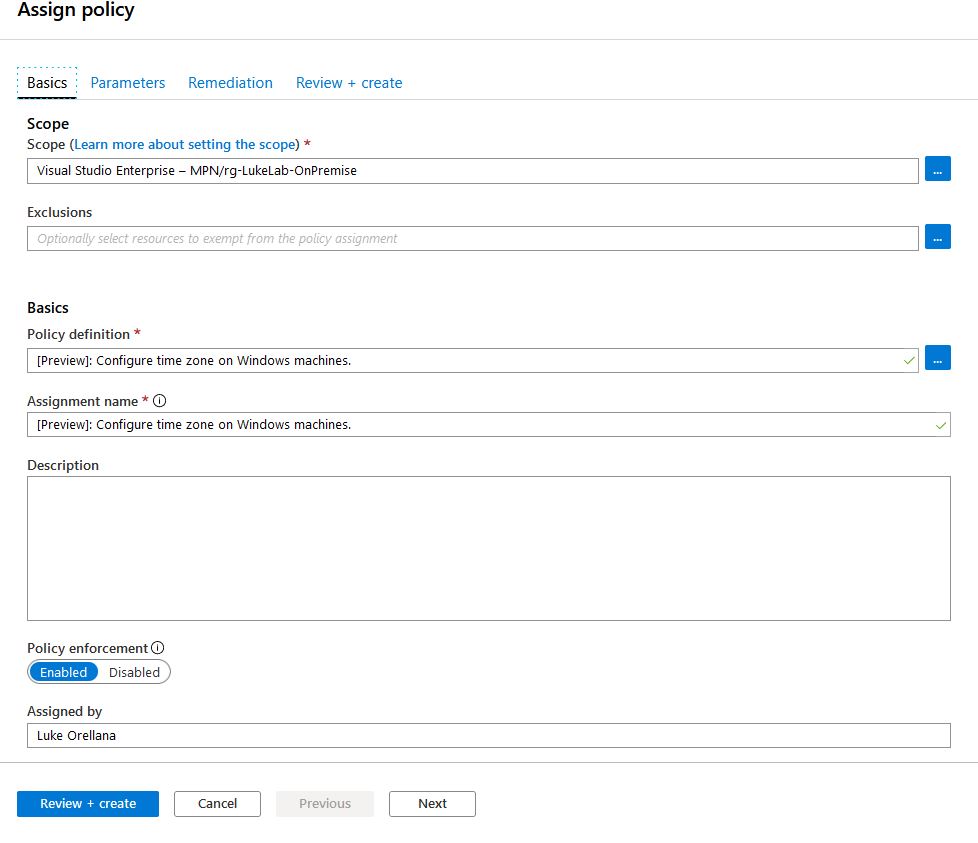
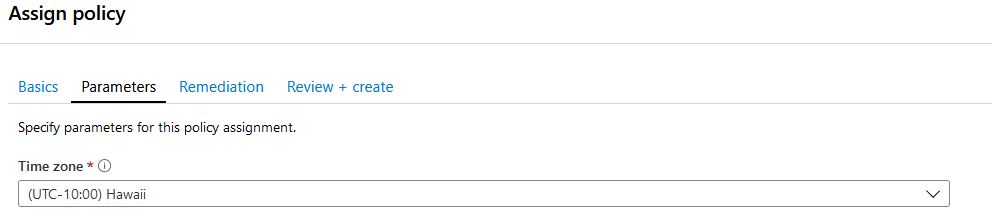
We will configure Web1 to always have the “Hawaii” timezone set. Also, we will check the “create a remediation task” to enforce this policy on the resource group right now:
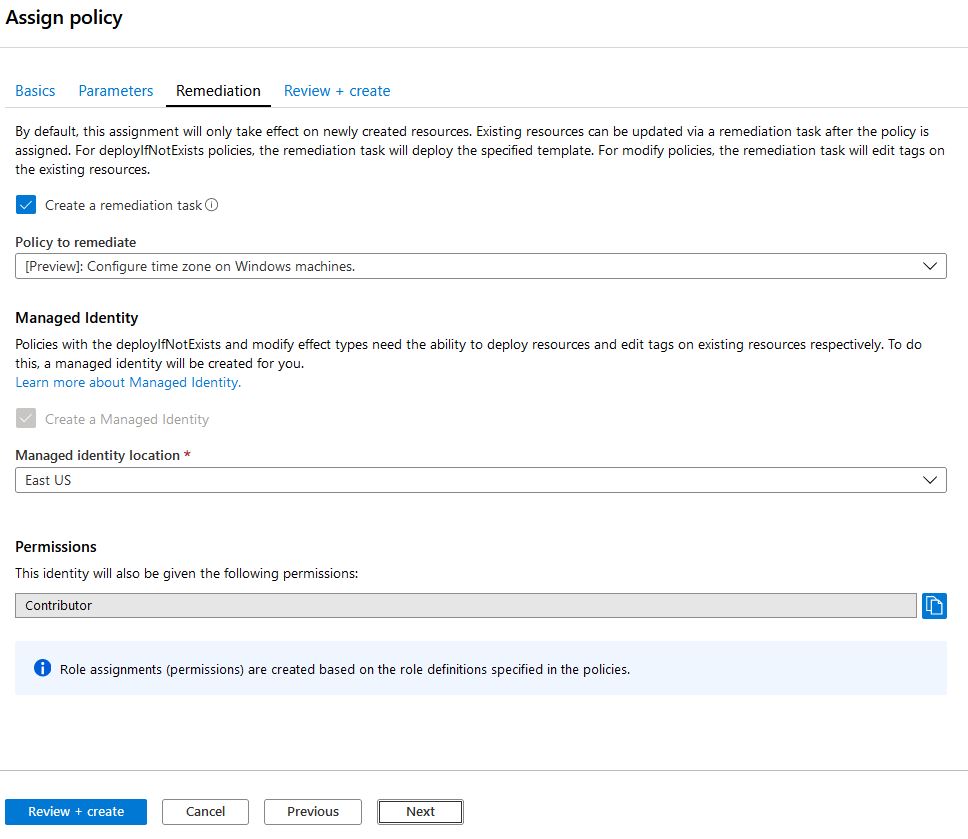
During the remediation process we can see that it is evaluating the assigned scope:
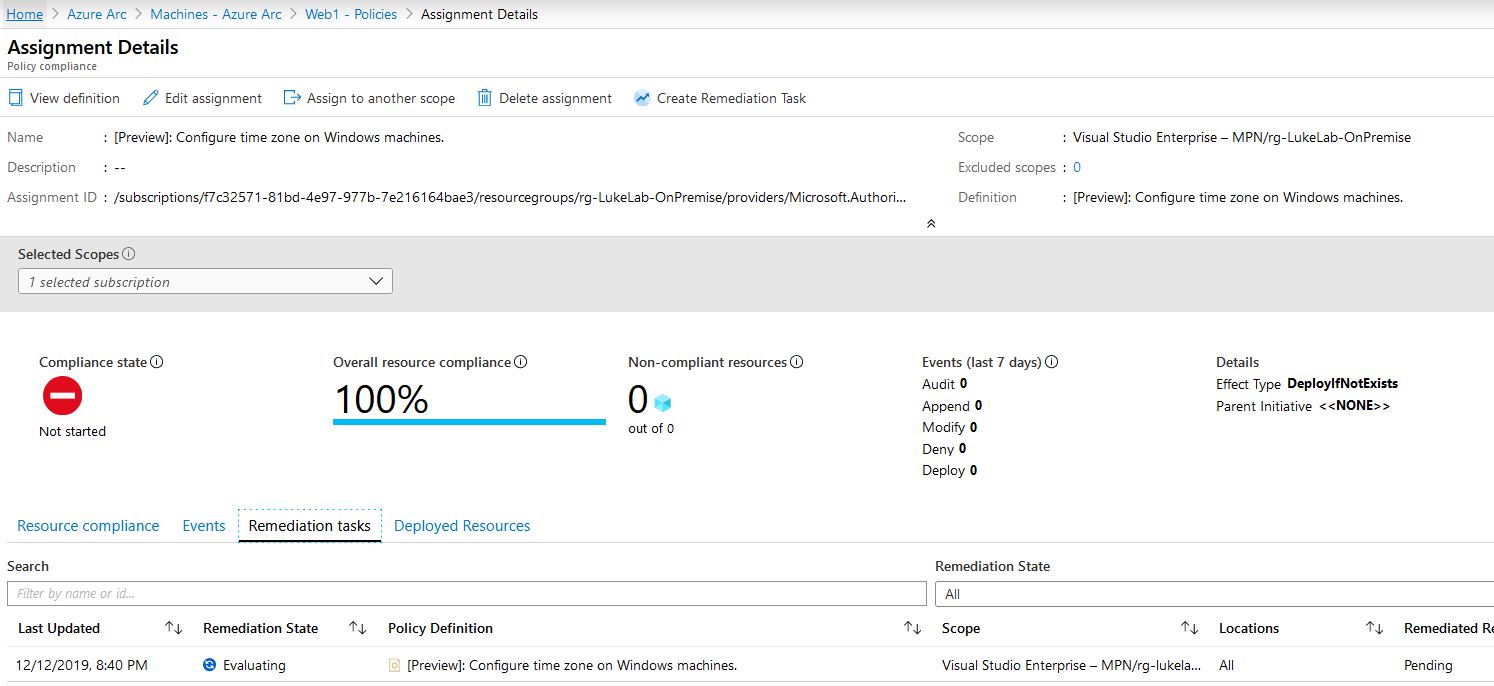
In a few minutes our resource is now compliant: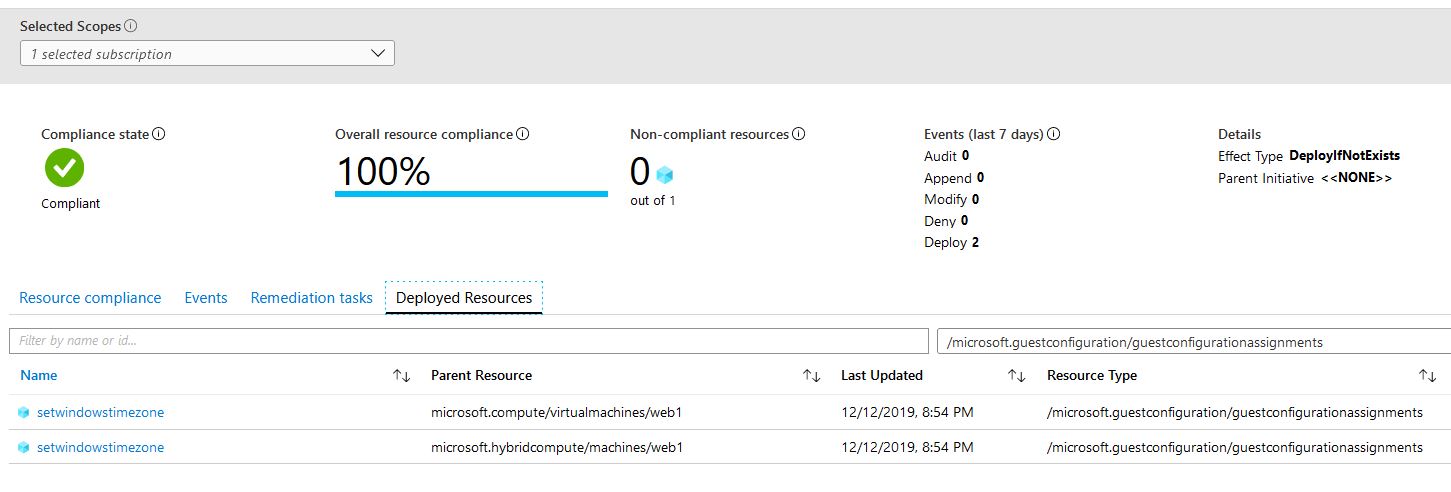
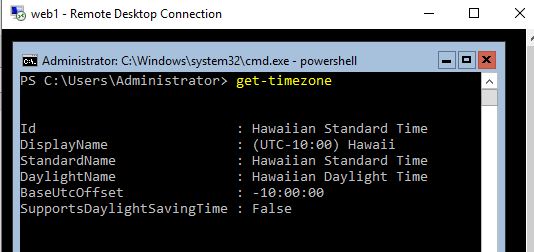
When we check Web1 we can see that the time zone has been changed:
Just the Beginning
Microsoft has big plans for Azure Arc. More and more policy definitions will become available bringing more functionality to the service. This is a big play on Microsoft’s part and really shows their stance on multi/hybrid cloud environments. It could potentially become the answer for solving the management headaches that come with the cloud and could make compliance and governance with VMware and Azure much easier.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!