Save to My DOJO
Table of contents
KeePass is one of the most widely used password management tools used today in IT. It’s simple to use and secure, which meets the needs of most businesses. Also, the fact that it’s open source goes a long way for the community to trust its code and ensure it’s not stealing customer data.
It is one of the top free tools an MSP can use for password management. To top it all off, a PowerShell module is available for automating and managing KeePass databases. This is incredibly useful for MSPs as they usually have a tough time tracking all the passwords for their clients and ensuring each engineer is saving the passwords to KeePass for each project.
Automating an ESXi host’s deployment, generating a new password, and then automatically storing it without any human intervention is a godsend. I can’t count how many times I’ve run into an issue where a password was nowhere to be found in KeePass or was typed incorrectly into KeePass. Quite simply, if you’re an MSP managing a large number of systems, you need KeePass, and you need to automate it. Here’s how.
Getting Started Automating with KeePass
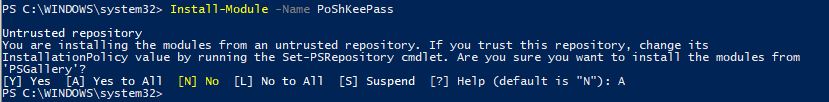
If you don’t have KeePass, you can download it here. Also, you can get the module from the PowerShell Gallery here. Or on a Windows 10 machine open up an administrative command prompt and type:
Install-Module -Name PoShKeePass
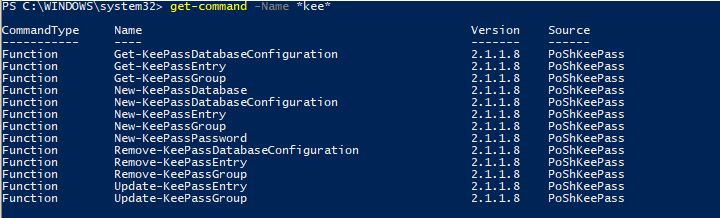
Now when we run a quick Get-Command search, we can see we have our new KeePass functions and we’re ready to go!:
get-command -Name *kee*
Connecting With KeePass
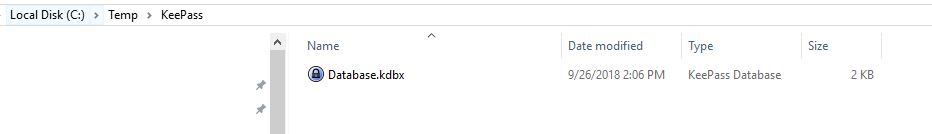
First, we need to establish our connection to our KeePass database. I have a KeePass database created in a folder, notice the .kdbx file extension which is the database extension used for KeePass:
Now we will use the New-KeePassDatabaseConfiguration cmdlet to set up a profile for the connection to the .kdbx file. We will also use the -UserMasterKey parameter to specify that this KeePass database is set up to use a Master Key. There several different ways of configuring authentication to a KeePass database, but for the purpose of this demo we are going to make it simple and use a MasterKey which is just a password that is used to access the database:
New-KeePassDatabaseConfiguration -DatabaseProfileName 'LukeLab' -DatabasePath "C:\Temp\KeePass\Database.kdbx" -UseMasterKey
![]()
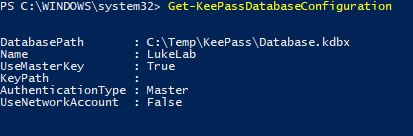
If I run Get-KeePassDatabaseConfiguration I can see my database profile is set up and points to the .kdbx:
Generating Passwords with KeePass
One really cool feature of the KeePass PowerShell cmdlets is that we can use KeePass to generate a password for us. This is very useful when setting unique passwords for each server deployment. This can be done with regular PowerShell coding, however, the KeePass modules allow us to generate a password in 1 line and on the fly without any extra coding. We will create our password variable and use the New-KeePassPassword cmdlet to generate a password. The parameters are used to specify the type of password complexity that we want:
$password = New-KeePassPassword -UpperCase -LowerCase -Digits -SpecialCharacters -Length 10
![]()
Now when we inspect our $password variable we can see that its a secured KeePass object:
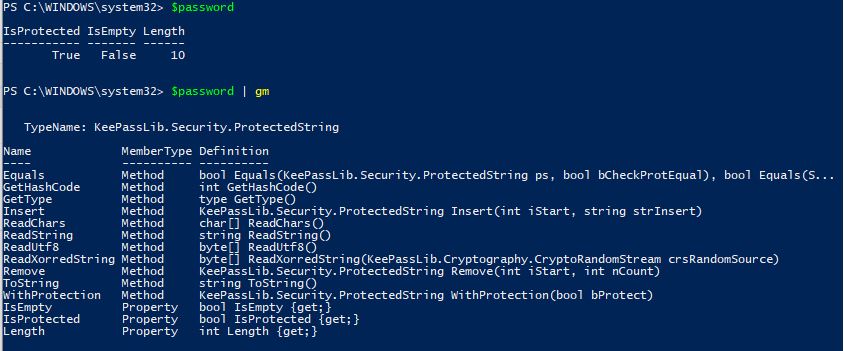
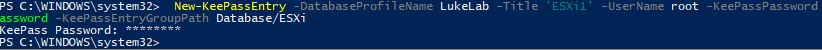
Now let’s upload a new entry to our KeePass database. Let’s say we are deploying an ESXi host and want to generate a random password and save it to our KeePass database. We will use the New-KeePassEntry cmdlet and specify our profile “LukeLab” that we set up earlier. We are also going to use our $password variable as the password profile that we want to use for the password complexity requirements. Then we get prompted for our Master Key password:
New-KeePassEntry -DatabaseProfileName LukeLab -Title 'ESXi1' -UserName root -KeePassPassword $password -KeePassEntryGroupPath Database/ESXi
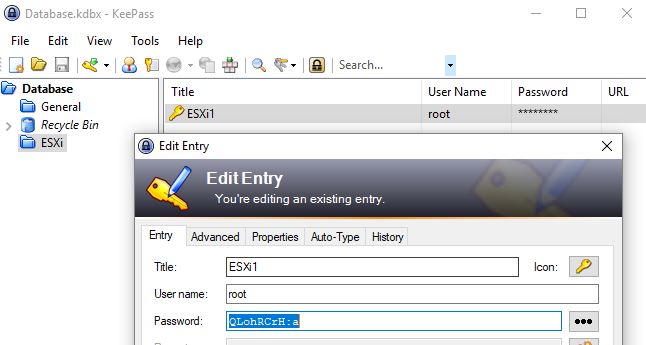
Now, when we open up our password database we can see our new entry and a randomly generated password:
Updating A KeePass Password
Password rotation is now becoming a normal standard within IT. Security is bigger than ever, and the need to change passwords every so often has become a necessity. Luckily, with KeePass and PowerShell, we can create scripts that automate the process of changing our ESXi host password and then update the new password in KeePass. We start by collecting the current KeePass entry into a variable by using the Get-KeePassEntry cmdlet:
$KeePassEntry = Get-KeePassEntry -KeePassEntryGroupPath Database/ESXi -Title "ESXi1" -DatabaseProfileName "LukeLab"
![]()
Next, we use the Update-KeePassEntry cmdlet to update the entry with a new password.
Update-KeePassEntry -Title 'ESXi1' -UserName root -KeePassPassword (New-KeePassPassword -UpperCase -LowerCase -Digits -SpecialCharacters -Length 10) -KeePassEntryGroupPath Database/ESXi -KeePassEntry $KeePassEntry -DatabaseProfileName 'LukeLab'
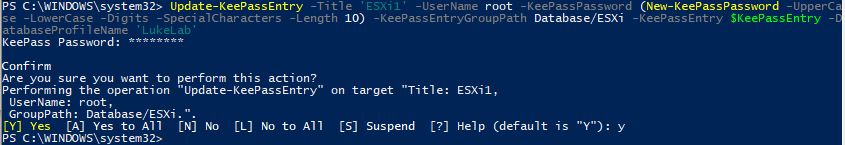
Now when we look at our password entry for ESXi1 we can see it has been updated with a new password:
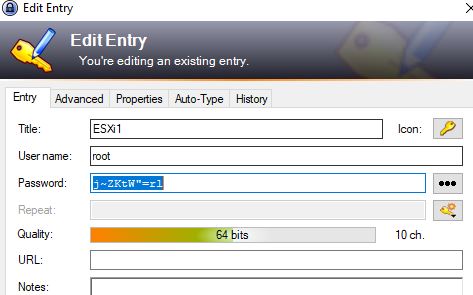
Now let’s update our ESXi system by obtaining the secure string from the new Entry and changing the password on the ESXi Host.
We save our entry to a variable again:
$KeePassEntry = Get-KeePassEntry -KeePassEntryGroupPath Database/ESXi -Title "ESXi1" -DatabaseProfileName "LukeLab"
Now we have our password as a secure string. If we look at the properties using $keepassentry we can see the secure string object is there:
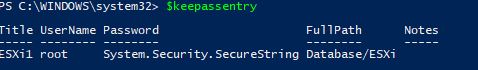
So now we can use this variable to create a credential object and pass that along to a script and change the ESXi password to this new password:
$newcreds = New-Object System.Management.Automation.PSCredential("Root",$keepassentry.password)
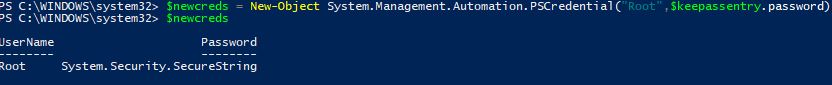
And, just to prove it, I can use the GetNetworkCredential method and show the decoded password is the same as that is in our KeePass:
![]()
Wrap-Up
This is a very powerful module as it allows IT Pros to automate the way they manage and enter passwords. There are many more capabilities than the KeePass module allows us to do, and the module author is expanding on more and more advanced features. This is an exciting time to be in IT, where we are able to use an assortment of PowerShell modules to accomplish feats that were nearly impossible only a few years ago.
What about you? Do you see this being useful for your engineers? Have you used KeePass for password tracking before?
Thanks for reading!


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









74 thoughts on "Building PowerShell Tools for MSPs: Automating KeePass"
Hi, the steps seems to be lacking as I couldn’t connect to an existing KeePass database even when I configured the master key using the KeePass App itself.
Hi Mon! Did you end up having any success with this? Does it throw an error?