Save to My DOJO
Table of contents
As some of you may already know, I have a bit of a soft spot for Azure Networking and the Azure Network Service. One service I have a real close eye on and work with during my daily business is Azure Virtual WAN. At Ignite 2020, my personal friend and Principal Program Manager for Azure Virtual WAN, Dr Reshmi Yandapalli, presented some exciting updates that I want to breakdown for you. Let’s get going!
Azure Virtual WAN Overview
In the first part, she covered the “What is Azure Virtual WAN”. I’m working with the Altaro team on a more detailed blog that will go into more detail about the technology and its applications but for now, let me show and summarize Reshmis Slides for you.
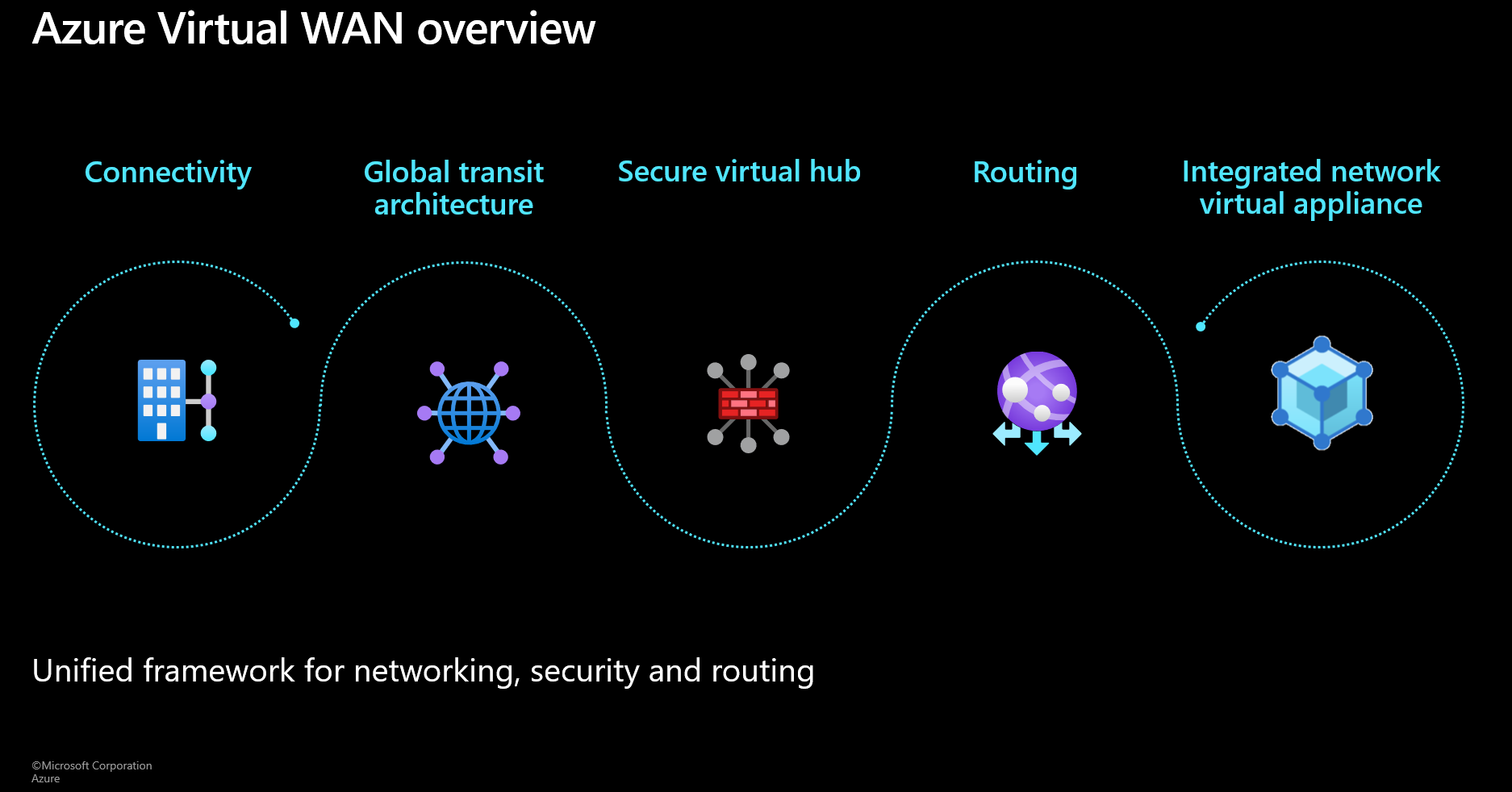
Azure Virtual WAN is a Unified, Microsoft Managed Framework which helps customers build a solid Backbone and Connectivity solution through the Microsoft Global Network.
The five patterns of Virtual WAN includes:
- Connectivity through Site to Site VPN, Point to Site VPN and Private Connectivity with ExpressRoute
- Global Transit Architecture
- Routing Services
- Security through Secure Hub Solution
- Integration of Network Virtual Appliances
Connectivity
Let’s take a look into the connectivity pattern in Virtual WAN and highlight the updates.
Site to Site VPN
As you may already know, the following features are already in production and are available.
- Supports IKEv1, IKEv2 protocol within the same Gateway
- VPN/SD-WAN CPE partnerships with signed agreements for configuration and connectivity automation. You can find the partnerships on this documentation page.
- Scale: Up to 1000 connections/region (hub), 20 Gbps aggregate throughput/region (hub)
The real change I want to highlight here is the availability of FQDN based IPsec tunnels and custom BGP/APIPA configuration.
For most of us, FQDN would be the most interesting feature. In the past, your connected branch locations needed to have a static IP for the IPSec tunnel, or needed to have supported devices from one of the partners for automated deployment. With the feature, you can just create a DNS space and use dynamic DNS updates like from DynDNS or NoIP to update the FQDN. That makes it possible to use Mobil or non-static IP connections for your branches. The use of those connections saves you parts of your budget and makes site connectivity much more flexible.
Did you know that you can create a Dynamic DNS service using Azure Services? The guys from Cirrius Tech wrote an awesome blog post about that so I won’t cover that here.
Point to Site VPN
Again, these features are already in production and working great.
- Support IKEv2, OpenVPN protocol, cert based and RADIUS authentication
- Built-in traffic management, Integrated with Azure VPN Client
- Scale : Up to 10K users/region (hub), 20 Gbps aggregate throughput /region (hub)
The major improvement in Point to Site is the option to configure a custom DNS Server for you Point to Site connections. During the whole COVID19 crisis, we saw a high adoption of Virtual WAN Point to Site and we noticed a big gap in the product, mainly with VPN Clients like the Windows 10 and the Azure Open VPN Client, who get their DNS configuration from the Point to Site Gateway in Azure. With a regular Virtual Network, that was not an issue. You just need to add the custom DNS to the virtual network DNS configuration.
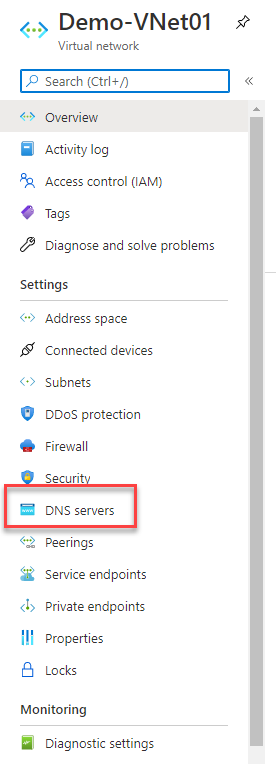
In Virtual WAN, you needed to contact the support to set it in the backend. With the recent update, the team enabled the custom DNS configuration which enables customers to perform the same configuration in Virtual WAN like they are able to do in a non managed virtual network.
Private Connectivity using ExpressRoute
Following features are already are in General Availability.
- Support encryption with native site-to-site VPN
- Scale : Up to 20 Gbps aggregate throughput /region (hub)
The most significant changes announced are:
- You can now connect up to 8 ExpressRoute Circuits to the ExpressRoute Gateway in Virtual WAN instead of 4, like in the past
- Now it is no longer needed to use an ExpressRoute Premium to connect an ExpressRoute Circuit to Virtual WAN. You now can use the Standard SKU and you will still be able to connect to Virtual WAN.
For me personally, the highlight is the reduction of the requirements for the ExpressRoute SKU. Especially if you stay within one of the geopolitical regions. With that reduction, you can save a lot of money.
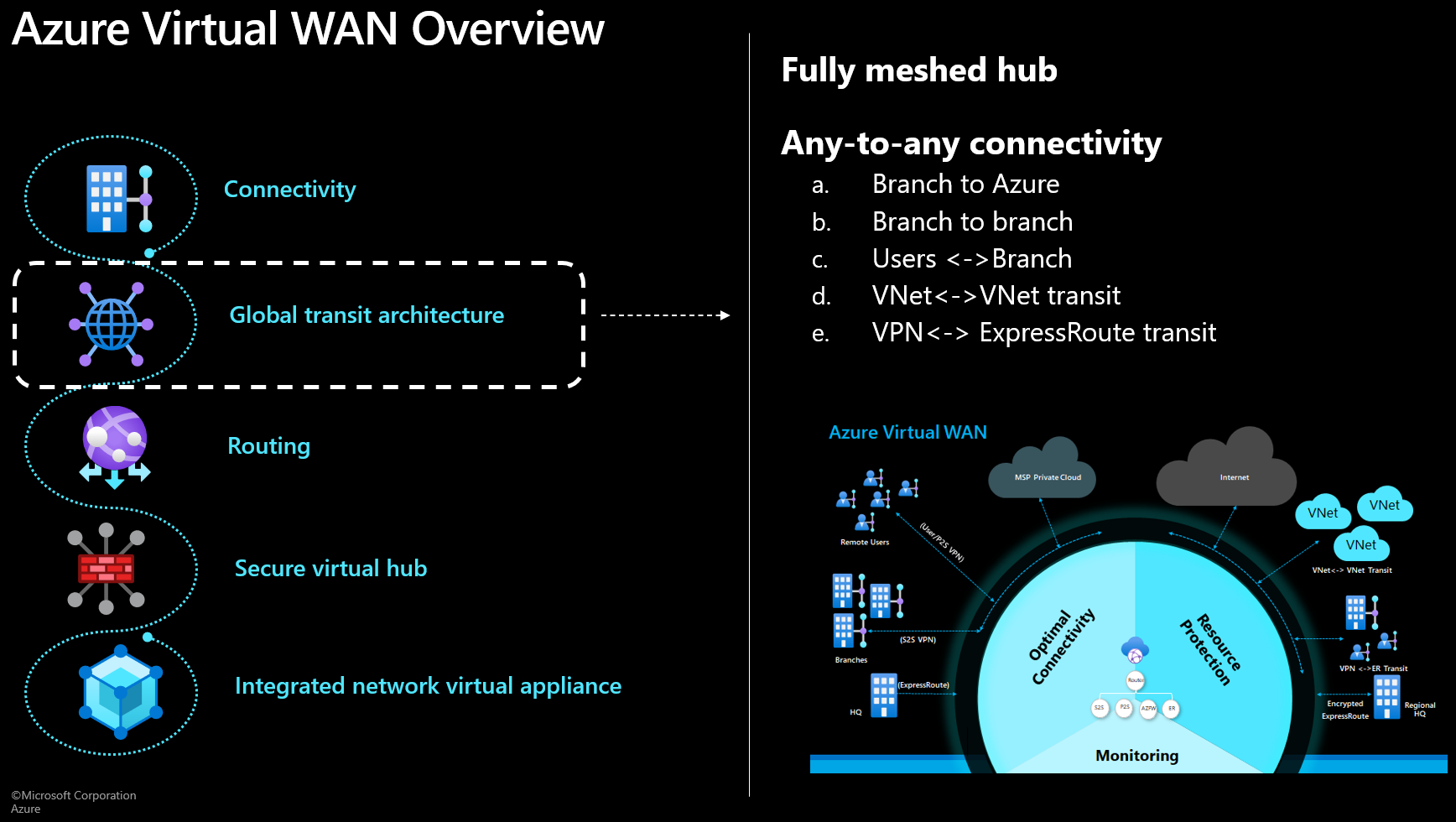
Global Transit Architecture
In Global Transit, there is no major announcement as you can see in Reshmies following slide. Virtual WAN stays within the Microsoft Managed Global fully meshed hub architecture.
Routing
There are two major announcements in routing. The first one I would like to mention is the throughput capacity. Virtual WAN routing is able to allow the customer up to 50 Gbps aggregated throughput. The next one and the most important release we saw yet with Virtual WAN is Custom Routing. Custom Routing enables a wide range of routing scenarios which makes solutions possible which are able to compete with regular network service provider offerings.
The links below represent a few of these documented scenarios. Please feel free to contact your Microsoft Account team or FastTrack for Azure to discuss your scenario.
- Scenario #1: Any-to-any
- Scenario #2: Isolating VNets
- Scenario #3: Custom isolation for VNets
- Scenario #4: Route to Shared Services VNets
- Scenario #5: Route traffic through an NVA
- Scenario #6: Route traffic through NVAs – custom
- Scenario #7: Azure Firewall – custom
Reshmi goes through those scenarios during her session and explains them briefly.
Secure Virtual Hub
Secure Virtual Hub makes improvements into the integration in Virtual WAN. It adds security and internet break out as a service to vWAN, and with CheckPoint, we get another endpoint security partner.
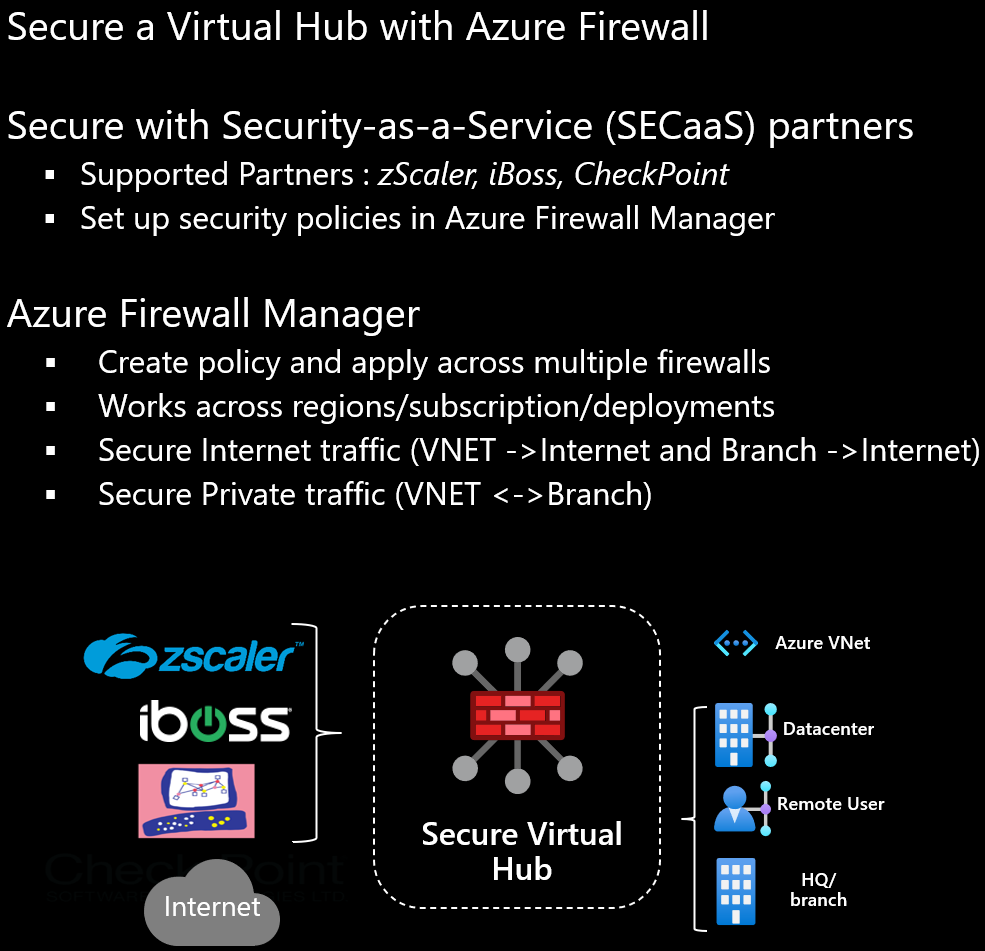
By the way, did you know that you can establish a secure Internet Breakout via a secure hub and the security partners to access services like Microsoft 365? With the global transit architecture, you can use a VPN or ExpressRoute to get a private connection or a doubled encrypted connection to Microsoft 365. If you want to read more on that scenario, please leave me a comment. 🙂
Integration Network Virtual Appliance
One major announcement for virtual WAN was the partner offering with Barracuda Networks, to put their Network Virtual Appliances into Virtual WAN Hub and with that directly into the Microsoft Azure Infrastructure. Together with Barracuda, Microsoft now offers Customer managed NVAs in Microsoft Infrastructure.
The offering can easily be configured via the Azure Portal as a Marketplace solution.
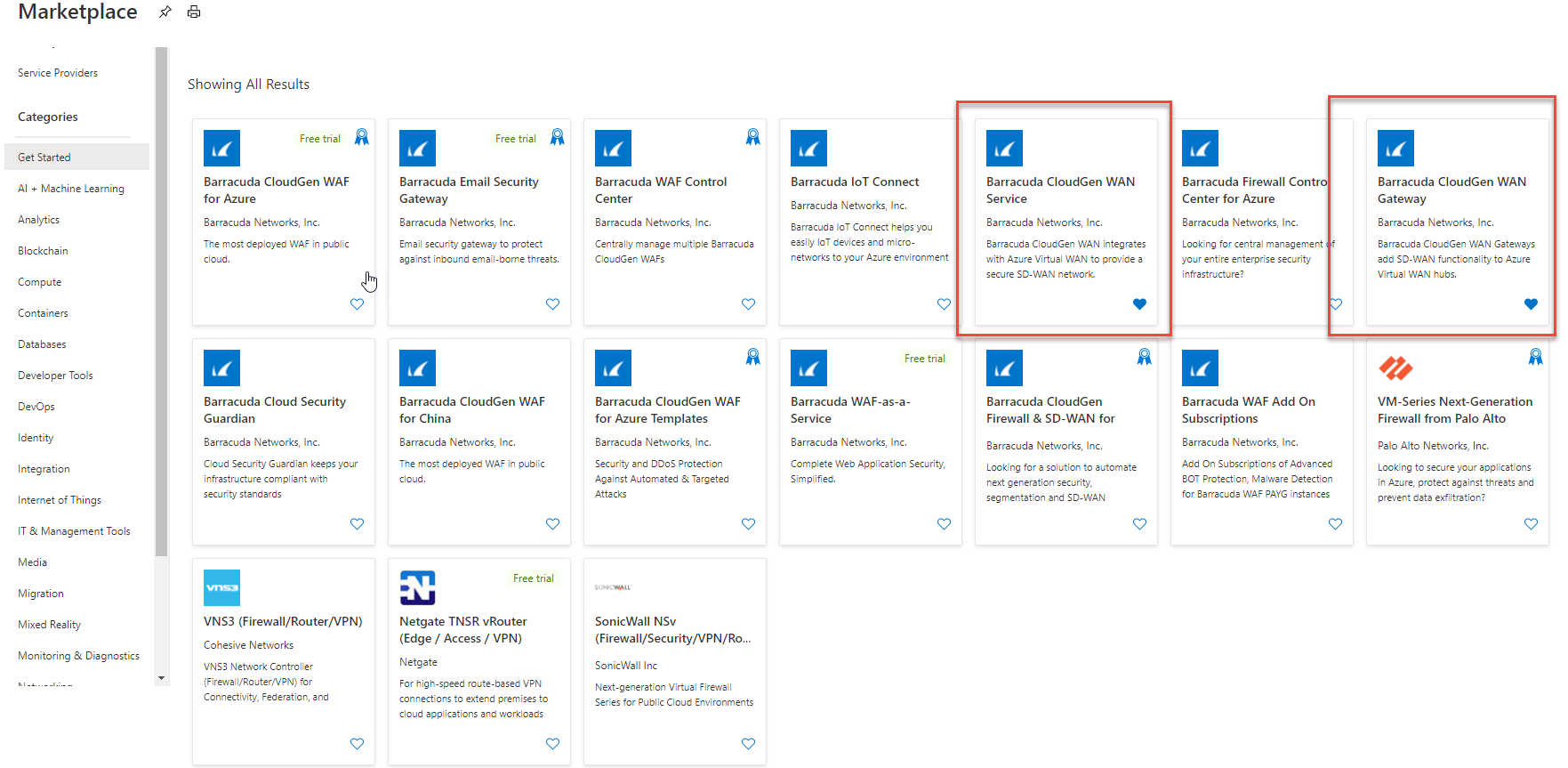
Now the NVA Team around Scott Napolitano and Sunil Kishin onboarded the next partner. I’m happy to say that Cisco Viptela joined the pack and will offer their NVAs in Virtual WAN going forward.
There are some major differences between an NVA in a regular self-managed virtual network and in a virtual WAN. In a regular virtual network, a customer needs to take care of redundancy and the route integration using user-defined routes. Within virtual WAN, redundancy is managed through the managed service in virtual WAN and the NVA Partner deploys the redundant solution to the virtual WAN Hub. Within a regular virtual network, the Network Virtual Appliance becomes the central routing instance, within virtual WAN the Network Virtual Appliance “speaks” Border Gateway Protocol Routing to integrate with the Virtual WAN Routing Service.
This kind of implementation makes setup much more reliable and flexible.
Putting it all together
As you may have already noticed, Virtual WAN is a manageable, but still complex solution, that is why I really love Reshmis “Putting it together” Slide and explanation during her session.
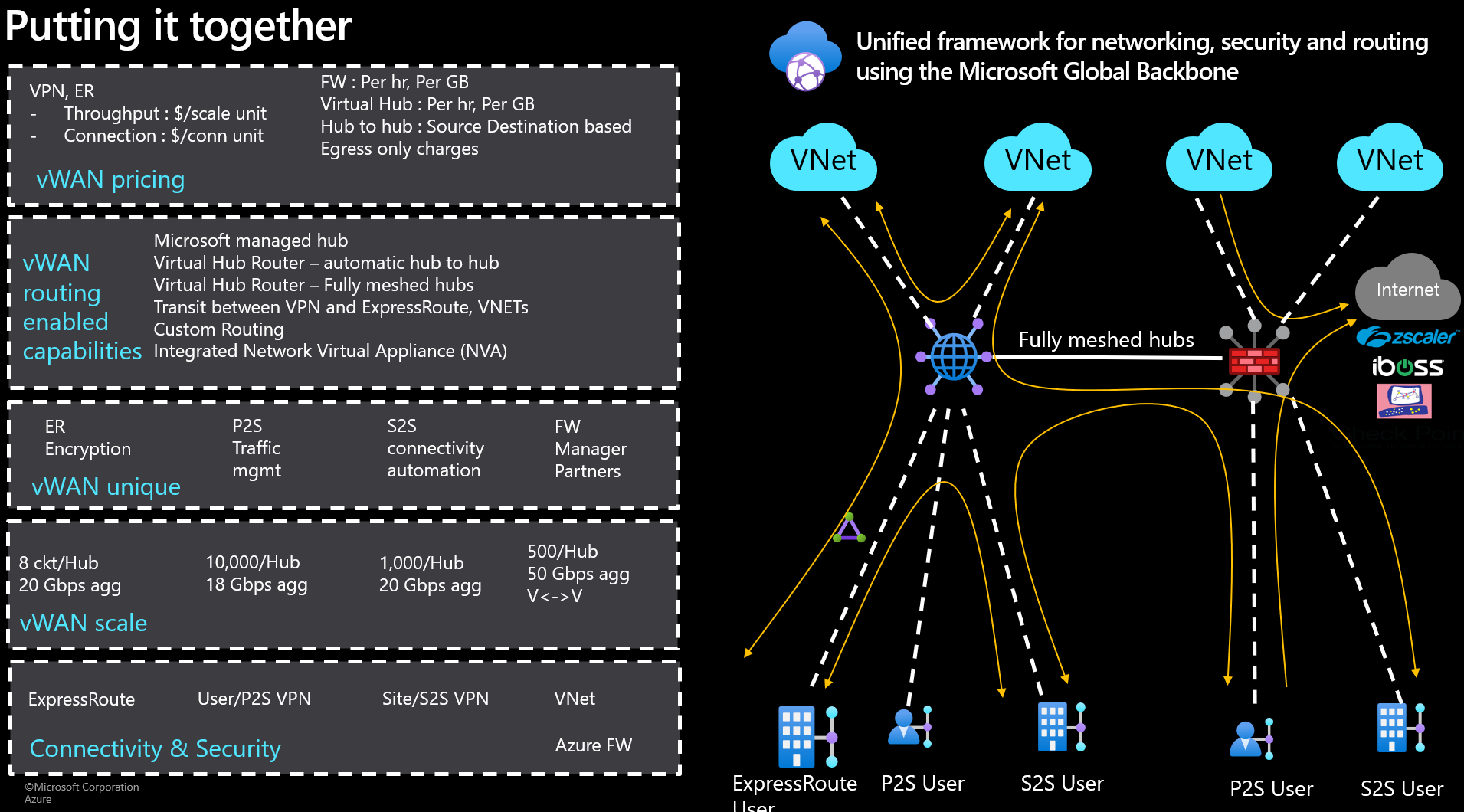
One thing I would like to mention at this point is that Reshmi did the whole session in one take without any stop or redoing a sequence. Very impressive. 🙂
Monitoring
A thing many customers were missing in Virtual WAN and which was a common feature with Virtual Networks, was the point of monitoring. The team answered and added the Virtual WAN Monitoring Preview as shown in the screengrab picture below.
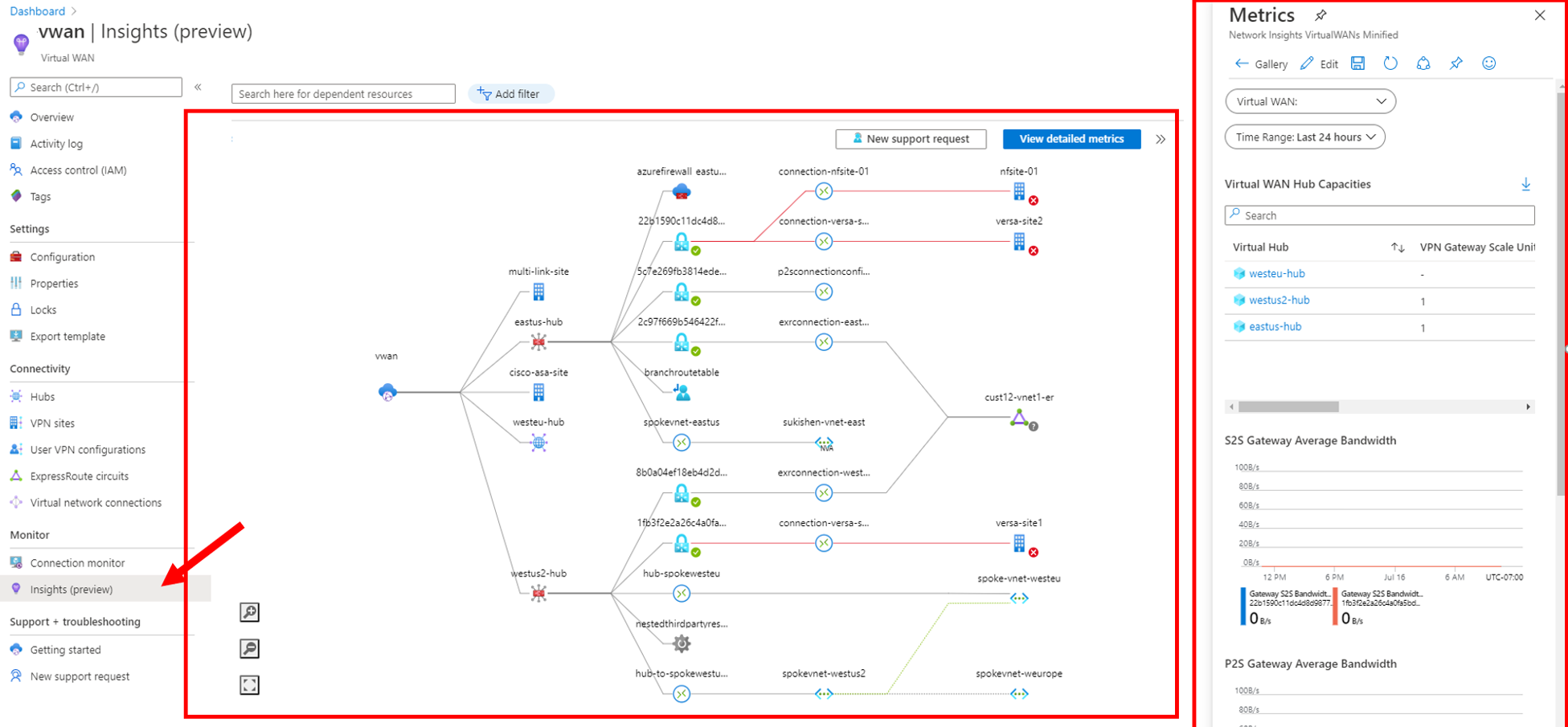
The Microsoft Virtual WAN Product Team uses Insight to give customers a detailed view on Bandwidth, Telemetry and path information.
Closing notes
So, those are my highlights from Reshmi’s session on Azure Virtual WAN. In my opinion, this was an amazing session and Virtual WAN is a hidden champion and could really be a serious gamechanger for the connectivity market in the future. Stay tuned as I will provide you with more deep dives into virtual WAN in the future together with our friends from Altaro Software.
If you want to learn more about the major announcements made at Microsoft Ignite, check out Eric’s breakdown of Satya Nadella’s Microsoft Ignite 2020 Keynote.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









