Save to My DOJO
Cybercriminals devastate organizations around the globe by locking up computers and encrypting data, then demanding thousands of dollars for the decryption keys. This type of malware, known as “ransomware,” represents one of the greatest security threats to technology infrastructure. It has caused the complete failure of some organizations. This article teaches you the best practices for protection from ransomware and allows you to educate your staff, harden your Windows ecosystem, and protect your backups from infection.
Educate Yourself for Protection from Ransomware
Ransomware usually enters the organizations when unsuspecting non-technical users download comprised files. Once activated, it runs with the security permissions of the account that opened it. The malware quickly spreads through the network, planting more copies of its executable as traps for other users. Then, it encrypts every file that it can access. Unfortunately, that includes backups and system recovery files.
Ransomware creators create variations rapidly, making it difficult for antivirus to detect. You only have two viable choices for recovery: pay the ransom or recover from a backup. Both options carry risks; many ransomware distributors will not provide keys after payment, and you might not have any useful backups that escaped the malicious encryption.
Educate Your Staff for Protection from Ransomware
Ransomware attacks usually start the same way as other types of malware: through a user that opens an infected file. User education is your most effective tool in ransomware mitigation. A few ways to approach staff training:
- Hold training sessions, create, and share material that explains social engineering, email scams, baiting, and phishing attacks.
- Teach users about the proliferation of infected files through download sites and e-mail.
The National Institute of Standards and Technology (United States) maintains a list of free and low-cost cybersecurity educational material. It includes a section on “Employee Awareness Training”.
Protect User Devices
Ransomware, like most other malware, enters through user devices. Focus the bulk of your technological ransomware protections there.
- Employ policies and programs to discourage or prevent users from accessing suspicious files. Filter emails with executable attachments and block users from enabling Microsoft Office macros.
- Enforce regular endpoint operating system and software patching.
- Deploy and maintain antimalware programs such as antivirus and intrusion prevention.
- Remove Adobe Flash and take steps to secure software that can run otherwise non-executable files, such as Java and web browsers.
- Prevent applications running from the AppData, LocalAppData, or Temp special folders.
- Install commercial web filtering tools.
- Block SMB shares on non-server systems.
Group Policy can help with some of these tasks.
Prevent Ransomware from Spreading
A proper defensive stance anticipates infection. Take these steps to proactively harden your datacenter to impede ransomware’s movement.
- Restrict administrative accounts to the fewest possible individuals and require them to use standard accounts for non-administrative functions.
- Create allow lists for known-good applications and block other executables.
- Firewall traffic into your datacenter.
- Shut down or block all unnecessary file shares.
- Disable user access to the volume shadow copy service (VSS).
- Audit and constrain users’ write permissions on file servers.
- Require users to store important documents in protected folders.
- Deploy intrusion detection tools.
- Do not map network shares to drive letters.
- Disable RDP, VNC, and other easily compromised remote access methods.
Train administrative staff on remote management tools, such as PowerShell Remoting, which can perform most tasks (including file copy) through a secured keyhole on port 5985 or 5986.
Protection from Ransomware for Backups
Properly protected backups will save your organization if ransomware strikes. Follow these best practices to secure them:
- Create and implement a thorough disaster recovery plan that includes regular full backups. Check out The Backup Bible for much more information on that topic.
- Use a Managed Service Account, not a user account, to operate backup
- Limit backup location ownership and write access to the backup application’s service account.
- Create a dedicated network for backup, isolated from user networks.
- If a vendor requires antivirus exclusions, ensure that their unprotected locations do not contain any data and remove any line of sight or access from their systems to vital network shares.
- Encrypt backups using a key saved to a location that ransomware cannot access.
- Capture frequent full offline backups.
- Frequently transfer full backups to cloud storage using a method that ransomware cannot hijack (such as a two-factor-protected vault)
- Regularly test your ability to restore from backup.
Group Policy can help with several of these points. Your backup software, such as Altaro VM Backup, can help with offline storage, offsite transmission, and encryption. Remember that some sophisticated ransomware knows how to operate backup programs, so you must always maintain offline backups.
You have multiple options for isolating networks. Most commonly, users must access server resources through firewalls and routers. Servers operate on their own network(s). You can then create a specific network just for the backup devices. Use your routers, firewalls, and access permissions to lock down ingress traffic for that network.
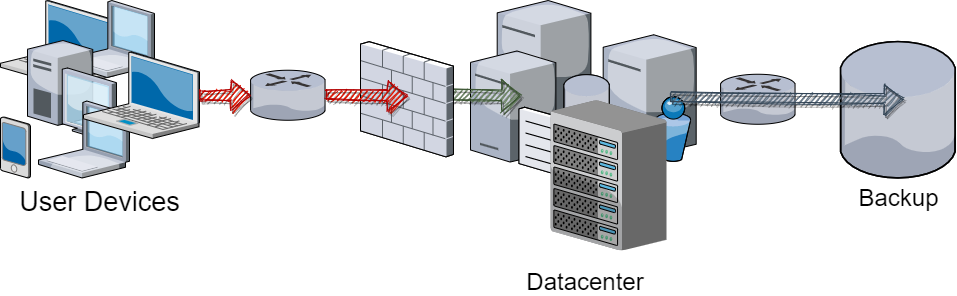
No single “right way” exists for isolating a network. At the extreme, you can completely isolate your backup network, known as an “air gap.” This requires all systems that participate in backup to have their own presence directly on the backup network. The network itself has no gateway or other connection to the rest of the network. A proper full air gap typically requires a fully virtualized datacenter to properly execute, as you have no other way to both provide network access from users to services and prevent network membership from servers to the backup network within the same operating system instance.
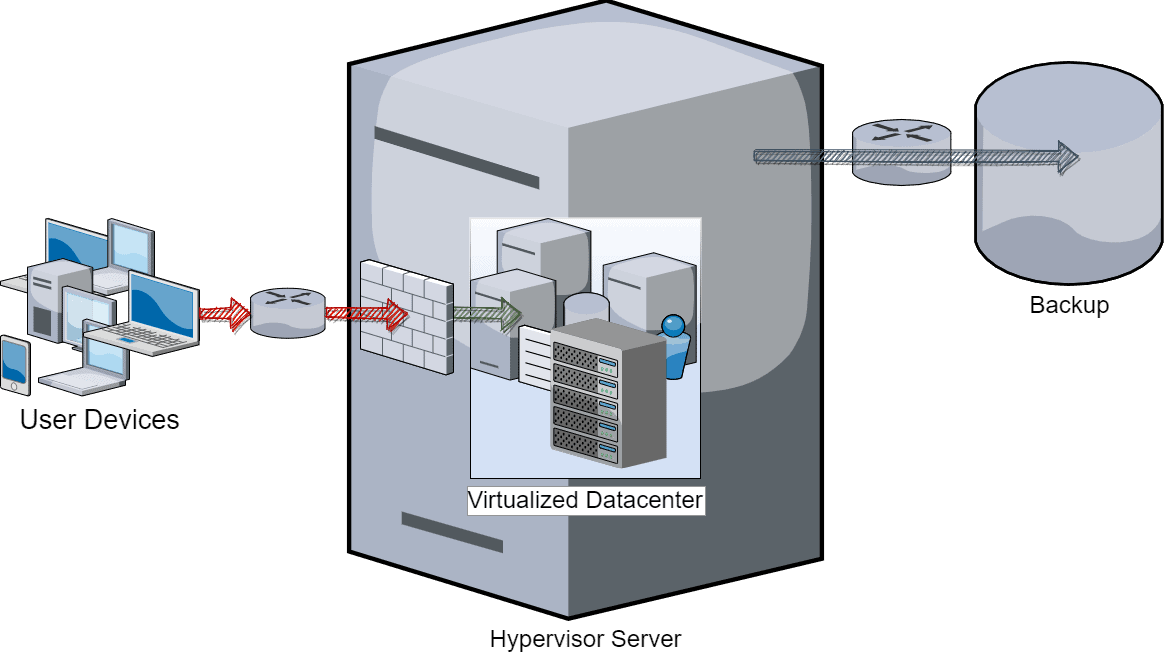
Complete air gaps require the hypervisor and backup systems to have no external network connectivity of any kind, which can make maintenance, patching, and offsite difficult transmissions difficult. Every compromise that you make to accommodate these problems reduces the effectiveness of the air gap.
Surviving a Ransomware Attack
These best practices can help you to mitigate your risks and minimize the spread of an attack.
- Immediately disconnect affected systems, including wireless and Bluetooth systems, from the network.
- If the ransomware has a timer that increases the bounty price or counts down to a full lockout, rolling back the BIOS clock may delay the trigger.
- Research the specific malware afflicting you. Many victims have shared their keys to older or well-known strains.
Protection from Ransomware and the Ongoing Journey
Nothing can fully protect you from ransomware, and this war will never end. Remain vigilant, keep watch on CVEs, and keep your backups and maintenance cycles in mind. The approaches presented here can ensure that you safely make it through an assault.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!