Save to My DOJO
Once upon a time, I wrote about using Client Hyper-V and toggling a guest’s Enhanced Session Mode off and on in order to use it as a sandbox environment. That procedure works, but many find it uncomfortable and it can require a fair bit of effort to use appropriately. A forthcoming Windows 10 feature will eventually make these kinds of activity easier. Currently called “Windows Sandbox”, you can find it in the current and future Windows Insider builds. I tried out the new feature and will take you on a tour.
What is Windows Sandbox?
You can read more details in the official announcement, which includes fairly in-depth technical information. Windows Sandbox combines features of virtual machines and containers to produce a lightweight, transient virtual machine. Unlike a traditional Hyper-V virtual machine, the management operating system runs Windows Sandbox more like a process than a traditional partition, giving it a performance profile more similar to type 2 than type 1. I want to call out a few key points:
- Transient: when deactivated, Windows Sandbox loses all changes and reverts to a fixed cold state.
- Clean: Windows Sandbox starts as clean as a new Windows installation at each startup.
- Minimal host impact: Hyper-V generally provides priority to the management operating system, but not in quite the same way as we typically think of process balancing. When you set a higher priority on a process within an operating system, that priority status does not bubble up to the hypervisor’s scheduler. So, the Windows Sandbox uses a new scheduler type that causes it to behave like a process within the management operating system. That will allow the host to prioritize its high-priority processes above the Windows Sandbox. Furthermore, Windows Sandbox will also perform a one-way mapping of host operating system executables into the sandbox’s memory space. You’ll see a greatly reduced memory load as a result.
- One-way: In addition to the memory mapping, operating system executable files are also mapped into the guest’s memory space. The Windows Sandbox instance cannot make any changes to memory mapped in from the host. Any modifications it makes to disk files occur only within Windows Sandbox.
- One at a time: You cannot run more than one instance of Windows Sandbox at a time.
- Pro or Enterprise at the minimum: Only the Pro and Enterprise SKUs will allow the feature. I can see a solid case for allowing the Home SKU to have it as well. However, with some monitoring, we can see that Windows Sandboxes uses some of the same components as Hyper-V, which does not ship in Home Edition.
Installing Windows Sandbox
First, you need to use a Windows build of at least Insiders 18305. I do not expect this feature to appear in mainstream releases any earlier than version 1903, due in March. As mentioned in the previous section, Windows Sandbox will only appear in the Pro and Enterprise SKUs.
You can find an entry for Windows Sandbox in the regular Turn Windows features on or off window:
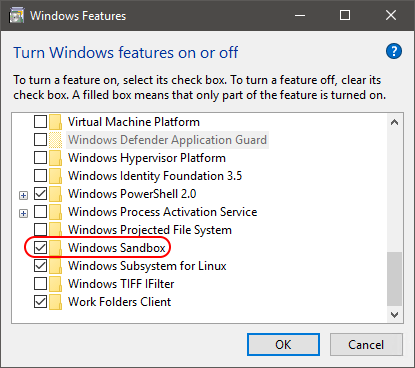
Oddly, I could not find any feature that seemed to match in dism.exe or Get-WindowsOptionalFeature.
Getting Started with Windows Sandbox
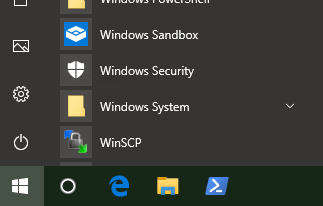
You’ll find a Windows Sandbox entry in the Start Menu:
The first time it starts up, Windows Sandbox needs to fully flesh out the base files into a usable container. On spinning disks, that will take several minutes. So, if you just see this splash screen for a while, hang in there:
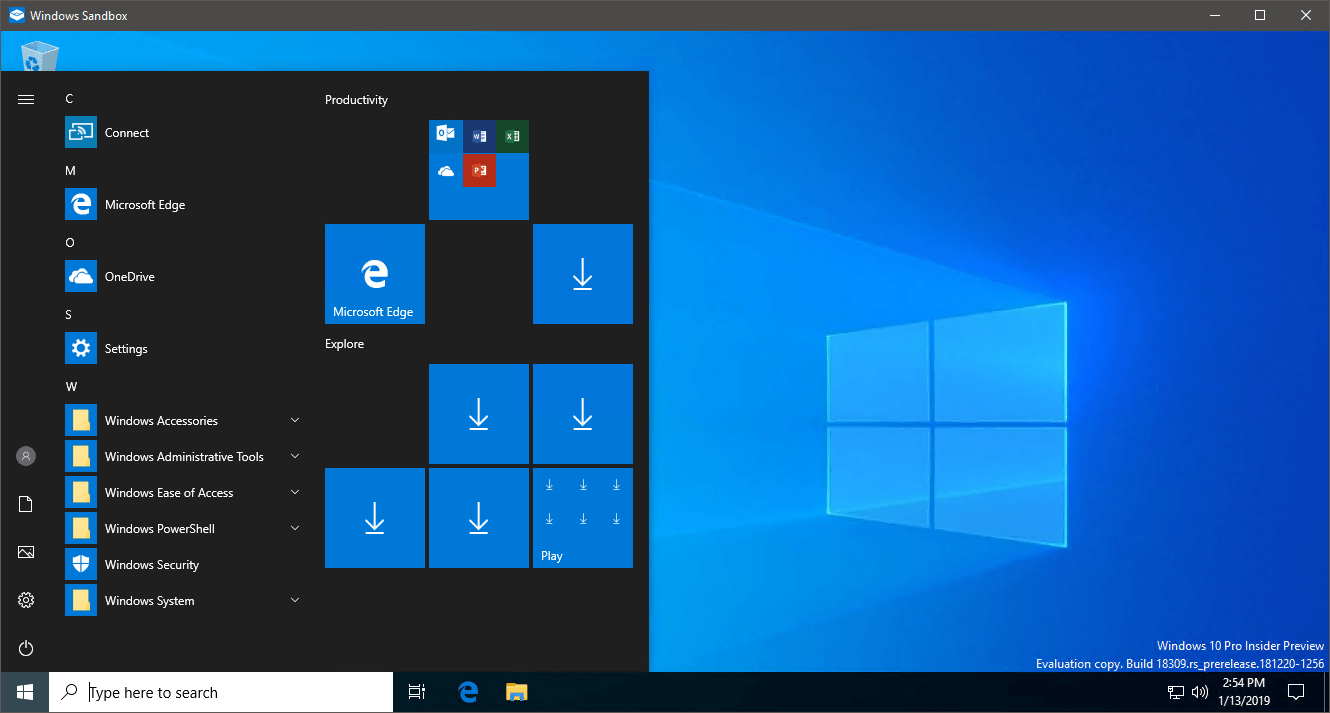
Once it boots, you’ll get a nice new Windows desktop running in a window:
If you check in System, you will find that it looks much like your local Windows install:
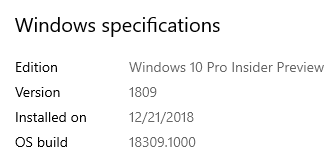
If you dig further, you’ll also find out that Windows Sandbox is considered an unactivated installation. I don’t know what would happen if you went through with the activation, but I recommend that you not waste any keys.

Also, notice that Windows Sandbox has NATted an IP for you so that you can have network connectivity. You can also see in this screenshot that you have a distinct user account when running in Windows Sandbox:
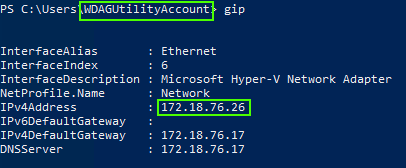
One other peculiarity: Windows Sandbox sets the timezone to the international dateline:

If you like, poke around a bit. You’ll find other oddities. For instance, you can’t enable other features.
When you’re done, don’t bother shutting down the running instance (caused errors when I tried). Just click the X on the Windows Sandbox title bar. It will prompt you to destroy the instance:
Next time you start Windows Sandbox, it should start faster.
Using Windows Sandbox as a Testing Tool
In case you have not encountered this term in the past, we use “sandbox” environments for safe testing. Whatever we put into a sandbox, we expect its effects to remain constrained to that sandbox. I intentionally used “safe testing” nebulously because it can mean many things. I feel that Windows Sandbox applies best to testing unknown executables that may contain malware. I will demonstrate that.
First, let’s place a diagnostic tool. We expect malware to attack processes in memory, the registry, or files. So, we want to monitor such activity. You have many options at your disposal to enact such monitoring. For this demonstration, I have selected a tool that most of us already know: Sysinternals’ procmon.
A Quick Introduction to Procmon (Process Monitor)
Like many tools of this kind, you will need to spend time making yourself familiar with it in order to use it effectively. I cannot show you much, but even a little knowledge goes a long way. Most importantly, spend a bit of time learning how to reduce the noise in the output. You have three main ways to achieve that objective:
- Directly exclude processes: right-click any item in the output window and click Exclude <process name>. This will filter all instances of that process out of the list:
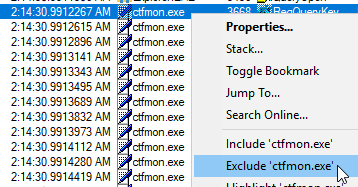
- Directly select processes: click and hold the target icon on Process Monitor’s toolbar, then drag it to the title bar of a program you wish to watch. You can also point to sub-windows, if necessary. Doing so will exclude all processes except the one that you highlight:
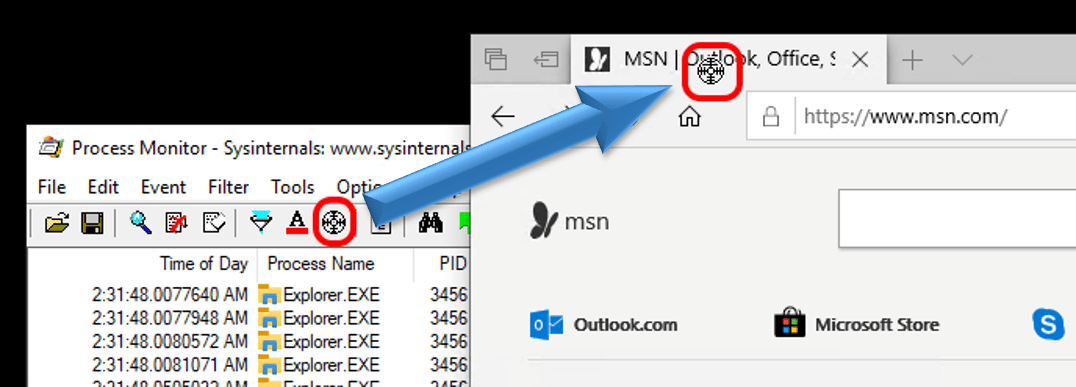
- Manually designate the filter: Click the filter icon on Process Monitor’s toolbar. This will open a small window that allows you to craft logic statements to include or exclude processes:
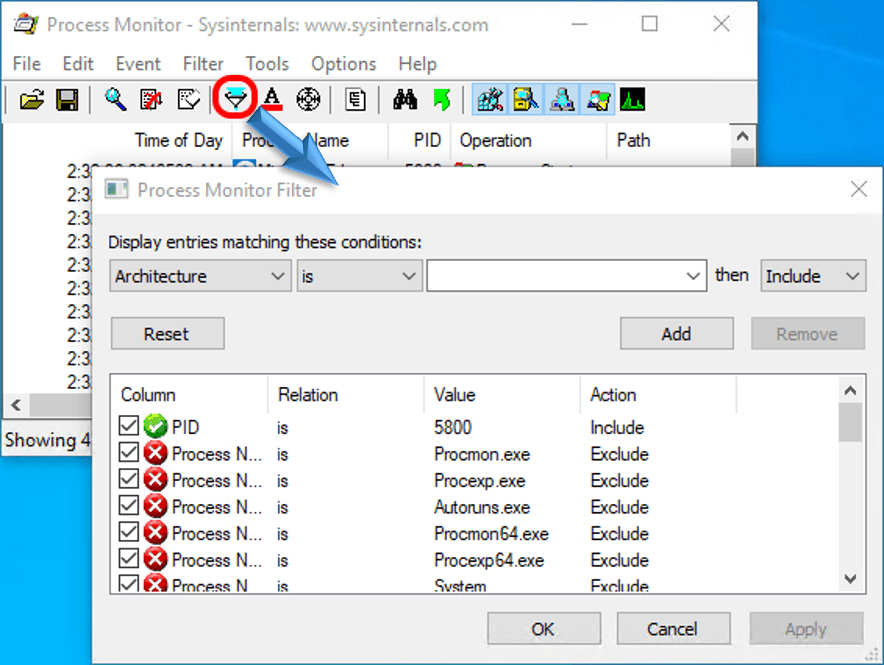
It does take some experience to use this tool at maximum effectiveness. When testing suspected malware, I recommend that you avoid selecting a single process. Expect nefarious applications to enlist legitimate processes to do their bidding.
How To Transfer Files into Windows Sandbox
You cannot use drag and drop to move items into the sandbox. However, you can use the clipboard to transfer files, text, images, etc. across the container boundary. So, just locate the files you want to try out inside Windows Sandbox and use whatever technique you prefer to place them on the clipboard:
Inside Windows Sandbox, use any of the normal clipboard tools to paste the file. You can place items directly on the desktop or in a folder, just as normal:
A Demonstration of Windows Sandbox
In addition to procmon,exe, I copied in a PowerShell script that I whipped up that will do significant damage to a system but will probably not trigger any antivirus tools.
I included the listing here, along with a first line that should hopefully stop casual copy/pasters from inadvertently wrecking their systems:
Write-Error -Message 'Have you lost your mind!?' -ErrorAction Stop
Get-ChildItem -Path $env:SystemDrive -Filter '*' -Recurse -ErrorAction SilentlyContinue | foreach {
if(-not $_.PSIsContainer)
{
Remove-Item -Path $_.FullName -ErrorAction SilentlyContinue
}
}
Without that first line, this script will delete all files on the local system drive.
Within Windows Sandbox, I first started up Process Monitor with a filter to reduce noise. Then, I started the PowerShell script:
In Process Monitor, I can see mass file delete events:
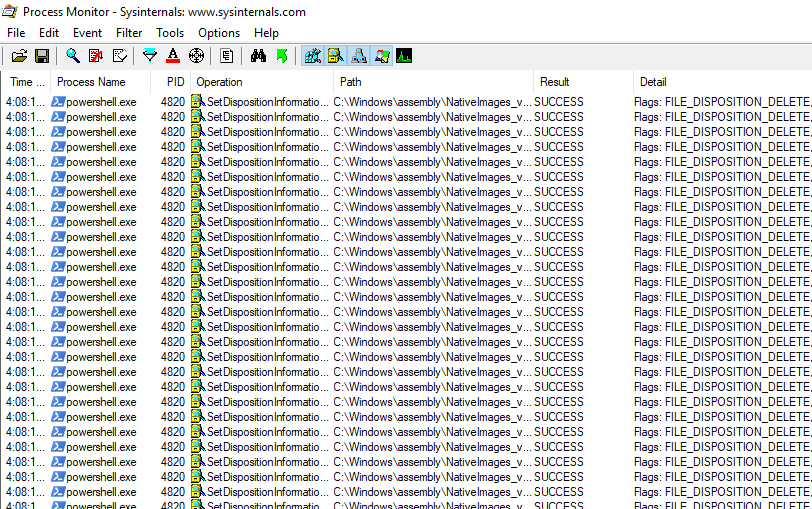
Be aware that even with a relatively tight filter, many other events still greatly reduced the visibility of these events. This particular script lists files prior to deleting them, so it generates a lot of its own noise. Of course, had I simply allowed the script to proceed through to its natural end, I would have noticed its damage. I would not expect such an obvious outcome from most malware. To get the most out of Windows Sandbox, enhance your digital forensics skills.
Limitations of Windows Sandbox
I like Windows Sandbox, but it does fall short of alternative approaches in some ways:
- Each startup is always pristine: Overall, a completely clean environment with a universally known state serves as a strength. However, you may quickly find tedium in needing to copy in tools at each new use. A single file copy, like procmon.exe, does not take much time. Moving in a larger tool, especially one that requires installation, may prove tiresome.
- No installable roles or features: Without the ability to install roles or features, you will have a limited testing scope. For instance, if you don’t trust one of my Hyper-V scripts, Windows Sandbox will not help you.
- No development interfaces: Sandboxes have many viable uses besides testing malware. Software developers use them to try out their work. Any computer user of any level might want to use one to try out some new application in a safe place before using it on their real system. Unfortunately, the simple copy/paste transfer method appears to be the only way to push files into Windows Sandbox. You can use Windows Sandbox’s network interface to connect to external locations, but you might find that prohibitive in some cases. No matter what solution you find, you may quickly find it tedious after only a few iterations.
It may be possible to place files prior to the startup of Windows Sandbox. I attempted a few different ways but never had any success.
You will need, at least for now, to continue using traditional virtual machines or containers if Windows Sandbox does not meet your needs.
Windows Sandbox Still Needs Some Development
I have read several reports of others facing troubles getting Windows Sandbox to work. Occasionally, I can’t get it to start without rebooting the management operating system. Sometimes, parts of it freeze up (like the Start menu and taskbar). Every now and then, the whole thing freezes up. Expect problems.
If you join the Windows Insider program, you can test Windows Sandbox and provide feedback that may aid in improving Windows Sandbox before it finds its way into an official release.
Windows Sandbox Internals
The release blog article contains a great deal of information on the internal functioning of the Windows Sandbox product. I will summarize a few points and add a few of my own discoveries.
- Windows Sandbox uses the base operating system files of your installed system to generate the sandbox image. It relies on a relatively tiny number of its own files.
- I mentioned Windows Sandbox’s memory sharing above. The article calls this technique “direct map”.
- I also talked about the way Windows Sandbox allows the management operating system to control the sandbox’s CPU utilization. The article calls this an “integrated kernel scheduler”.
- Windows Sandbox employs what the article refers to as “snapshot” and “clone” techniques to restrict file usage and duplication. I cannot directly determine how these map to the snapshot/checkpoint technologies in Hyper-V, although it stands to reason that they have at least some relation.
- The system uses apparently new, but vaguely-described graphics virtualization techniques. The article claims that you can smoothly run graphics-heavy applications within Windows Sandbox. Given the other limitations of Windows Sandbox, I am uncertain of the value of this technology. However, it may signal a future of graphics in Hyper-V.
- You can find the files for Windows Sandbox at C:ProgramDataMicrosoftWindowsContainers. Making changes appears to have no positive effect. I can stop Windows Sandbox from starting until I reboot the host, but then everything goes back to the same pristine environment.
- When a sandbox is active, you can see running vmwp.exe processes. That’s the same executable that Hyper-V uses with its virtual machines.
- If you run Windows Sandbox inside a virtualized instance of Windows 10, it will need to have processor virtualization extensions enabled.
Try Out Windows Sandbox!
If this new feature intrigues you at all, I suggest that you get involved with the Windows Insider program and take it for a spin. Let us know how your testing goes!


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!










7 thoughts on "What is Windows Sandbox Mode in Windows 10?"
Does enabling Sandbox have the same overhead on the OS itself as enabling Hyper-V? I know when just enabling Hyper-V there is resource overhead even when no virtual machines are running. Not sure if the same applies to Sandbox. I have Sandbox enabled in “turn features on and off” but Hyper-V is not checked. But sandbox still works fine. So I’m not sure if the same OS overhead (even when Sandbox is shutdown) applies here.
I haven’t done a lot of under-the-covers investigation. I know that it uses fewer resources overall, but I’m not certain how much. My understanding is that Sandbox is more of a type-2 design, so it can unload itself when it has nothing to run. Hyper-V can’t do that.