Save to My DOJO
What’s all the Fuss About?
Meltdown and Spectre have been the internet buzz words recently. These are huge exploits that have been around forever and are just now being discussed in the public media. Many sites explain how these two exploits work, however, the most simplified explanation I have found was from a user on a hacker news thread and they blew it out of the park when giving an analogy on how the vulnerability works:
“Let’s say you want to know if your boss is away on vacation next week
So, you call their admin and say, “If my boss is on vacation next week then I’ll need to check my contact info”.
They load up the boss’s calendar to check.
If the boss is NOT on vacation they don’t bother loading your info.
If the boss IS on vacation then they subsequently load up your info, ready to fulfill the second half of your request.
Then, the admin remembers the boss didn’t want you to know whether they are in or out. So, you hear back, “sorry, can’t tell you that”, but you follow up with “OK, well can you still double check that my phone number is…”
If they respond quickly with a yes, then your file is still on their screen and the boss is, in fact, out next week. If there is a short pause while they look it up, then it’s the opposite.”
So, in other words, Meltdown and Spectre are vulnerabilities that are used by making CPU executions and determining data from memory based on execution time. This process is called speculative execution and is now a game changer for all CPU manufacturers.
If you want a more in-depth look at how Meltdown and Spectre work, Bert Hubert did an awesome deep dive explanation here.
What’s the difference between Spectre and Meltdown? The biggest difference is that Meltdown can read the kernel memory on the OS. Spectre, on the other hand, can read the kernel memory on the hardware which even means access to VMs and the Hypervisor.
For most organizations, this isn’t a huge issue. They’ll patch the servers under their care, you may have to add some resources to deal with the performance hit that has been reported in the news, and life will go on. However, if you’re part of a larger organization or a team that manages hundreds or thousands of endpoints, like an MSP, then this can cause some really big headaches. What should you be doing about them? We’ve diluted the issue down to the essential info you, as an MSP, needs to know first and foremost with a list of articles and links to most major vendors to assist you in dealing with this issue.

Patching
As if IT Pros and MSPs weren’t busy enough, we now have to take the time to harden our environments and the environments we manage against these exploits. In the past few weeks, this has been an obscene amount of work with patching all hardware and OSes. A recent survey conducted by Barkley reveals that only 4% of Enterprises are fully patched against Spectre and Meltdown. In my attempt to make it a little easier for you, below I’ve placed some links to the hotfixes/statements put out by major vendors. Be sure to check each one that relates to your environment to determine what you can do to protect yourself against these exploits. Also note that many patches have been reported to have performance hits, so make sure you do your homework and test these patches thoroughly before applying them to production:
Notice: Several fake Meltdown and Spectre patches have been reported, make sure that you are downloading from a trusted source.
Cloud Vendors
This exploit is huge particularly for cloud providers hosting services with multi-tenants. These new vulnerabilities may easily allow access to data other customers. Here is what the two major cloud providers have stated so far so if you either of them you need to be aware of their official message:
For Windows: Your AV Package Must Support the Fix!
Take note that whatever AV you’re running, must support the hotfix provided by Microsoft.
Note from their KB:
Customers will not receive these security updates and will not be protected from security vulnerabilities unless their anti-virus software vendor sets the following registry key:Key=”HKEY_LOCAL_MACHINE”Subkey=”SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat”Value=”cadca5fe-87d3-4b96-b7fb-a231484277cc” Type=”REG_DWORD”
If you’re wondering whether your AV application works with the existing patches, there is a community-driven document that is keeping track.
Known Applications That Have Been Reported to Have Issues After Hotfix
SCCM – Reported issues with connecting to SQL after patch. Microsoft released a TechNet Bulletin for running SCCM with the patch.
Cisco AnyConnect VPN – Reported issues that Microsoft Cumulative update KB 4056894 may break this application
AMD – Microsoft has temporarily paused Windows OS updates to devices that have specific AMD processors. Microsoft has now released new patches for AMD that do not cause issues.
Various Anti-Virus Programs – Reported to cause blue screens.
Windows Servers and PCs – Reported slowness from applying hotfixes.
Citrix XenApp patches hit performance hard.
IOS 11.2.2 – Apple states what to do if their patches slow down your mobile phone.
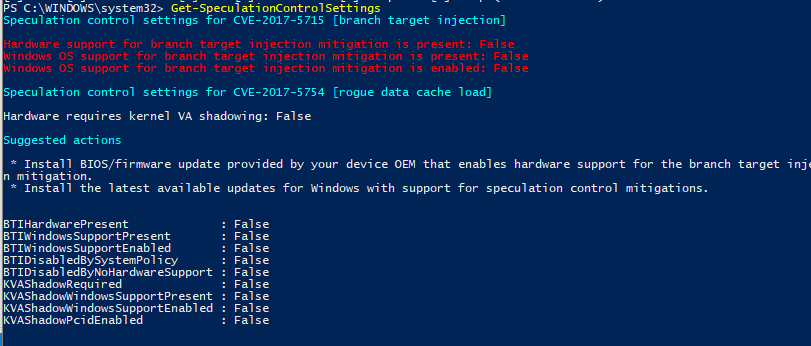
Microsoft’s PowerShell Script to Check for Vulnerabilities
Microsoft has released a PowerShell script on the PS Gallery that will check your workstation for vulnerabilities. It is very easy to run, just open an Administrative PowerShell console and type:
Install-Module SpeculationControl
Choose Yes to install the module and then type in the following command to check your device:
Get-SpeculationControlSettings
The information displayed will state whether you are protected or not, if the results are False like below, it means you are not protected:
What about Linux?
There is a script for Linux that will help detect the vulnerabilities as well.
More to Come!
I will be updating this post throughout the next few weeks with more information/links that become available. Be sure to check back, and, if you find something interesting please share it with us in the comments below!


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!








