Save to My DOJO
Table of contents
The File Server Resource Manager role provides many features. File screening, in particular, can be used to help mitigate damage from a ransomware attack. With file screening, file servers can be configured to perform real time auditing on all shares for any files that become modified to any known ransomware extensions. In the event of a user getting infected with ransomware, the file screen will detect the modification of the files and deny that user access to the file shares, preventing them from damaging any other files. This can save hours of downtime and clean up.
I have created a script that will set up and configure all of this within minutes. The script performs the following actions:
- Installs the file server resource manager role if it is not installed.
- Configures file server resource manager to screen for known ransomware file extensions.
- Configures the file screen to execute a script whenever a file is modified to a known ransomware extension. The script then blocks SMB share access to all shared files on the file server and sends an email message to whatever email specified.
The script requires the following prerequisites:
- Windows Server 2012 – in order to use the cmdlet that blocks SMB share access.
- Mail Relay Server – Used to configure email alert.
To create the powershell script, copy the code below into a notepad and save it as a .ps1 (for example, Install-FSRMRansomeware.ps1):
Update- Edited script to restart FSRM service after blocking SMB permissions. Ran into issue where the task was only triggering once.
function Install-FSRMRansomware {
<#
.SYNOPSIS
Installs the File Server Resource Manager role if not installed and then configured a file screen on all drives other than C.
The file screen screens for possible ransomware infections and then deny's SMB access to the user who trigged the screen.
.PARAMETER SMTPServer
Specify the address of an email relay server. This is used to send the alert emails that generate when the file screen is triggered.
.PARAMETER EmailTO
Specify the email address to send the alerts to.
.PARAMETER EmailFrom
Specify the email address that the email alerts are sent from.
#>
[CmdletBinding()]
param(
[Parameter(Mandatory=$True,
HelpMessage="Please input the address for an accessible email relay server.")]
[String]$SMTPServer,
[Parameter(Mandatory=$True,
HelpMessage="Please input a valid Email address to send the email alerts to.")]
[String]$EmailTo,
[Parameter(Mandatory=$True,
HelpMessage="Please specify an email address to recieve alerts from.")]
[String]$EmailFrom
)
Process{
#add the FSRM role if it doesnt exist
If ((Get-WindowsFeature fs-resource-manager).installed -like "False"){
Write-Verbose "Installing File Server Resource Manage Role"
Install-WindowsFeature fs-resource-manager
}
If ((Get-WindowsFeature RSAT-FSRM-Mgmt).installed -like "False"){
Write-Verbose "Installed FSRM RSAT Tools"
install-windowsfeature RSAT-FSRM-Mgmt
}
#Set notifications limit to 0
Set-FsrmSetting -EmailNotificationLimit 0 -EventNotificationLimit 0 -CommandNotificationLimit 0 -ReportNotificationLimit 0
#Create File Group for FSRM
New-FsrmFileGroup -name "Ransomware Files" -IncludePattern @( "*DECRYPT_INSTRUCTION.HTML*",
"*HELP_DECRYPT.HTML*",
"*decrypt all files*.bmp*",
"*.ecc",
"*.ezz",
"*.exx",
"*.zzz",
"*.xyz",
"*.aaa",
"*.abc",
"*.ccc",
"*.vvv",
"*.xxx",
"*.ttt",
"*.micro",
"*.encrypted",
"*.locked",
"*.crypto"
"*_crypt",
"*.crinf",
"*.r5a",
"*.XRNT",
"*.XTBL",
"*.crypt",
"*.R16M01D05",
"*.pzdc",
"*.good",
"*.LOL!",
"*.OMG*",
"*.RDM",
"*.RRK",
"*.encryptedRSA",
"*.crjoker",
"*.EnCiPhErEd",
"*.LeChiffre",
"*.keybtc@inbox_com",
"*.0x0",
"*.bleep",
"*.1999",
"*.vault",
"*.HA3",
"*.toxcrypt",
"*.magic",
"*.SUPERCRYPT",
"*.CTBL",
"*.CTB2",
"*.locky" )
#Create FSRM Template xml file and import template then remove xml file
$FSRMTemplate = @"
<?xml version="1.0" ?><Root ><Header DatabaseVersion = '2.0' ></Header><QuotaTemplates ></QuotaTemplates><DatascreenTemplates ><DatascreenTemplate Name = 'RansomwareCheck' Id = '{122F5AB4-9DF0-4F09-B89E-0F7BDC9D46CC}' Flags = '1' Description = '' ><BlockedGroups ><FileGroup FileGroupId = '{82D08F60-7319-4BE2-8621-066DB91A958E}' Name = 'Ransomware%sFiles' ></FileGroup></BlockedGroups><FileGroupActions ><Action Type="1" Id="{73AFB339-FF17-42DC-B9B9-E7C9A8E7C9A9}" EventType="2" MessageText="User%s[Source%sIo%sOwner]%sattempted%sto%ssave%s[Source%sFile%sPath]%sto%s[File%sScreen%sPath]%son%sthe%s[Server]%sserver.%sThis%sfile%sis%sin%sthe%s[Violated%sFile%sGroup]%sfile%sgroup,%swhich%sis%snot%spermitted%son%sthe%sserver." /><Action Type="3" Id="{D0B80CC5-E6DD-481C-9534-19944A851A72}" ExecutablePath="C:WindowsSystem32WindowsPowerShellv1.0powershell.exe" Arguments=""C:ScriptsScriptToDenyPermissions.PS1"" WorkingDirectory="C:WindowsSystem32WindowsPowerShellv1.0" Account="3" MonitorCommand="0" KillTimeOut="0" LogResult="1" CurrentSid="S-1-5-21-3468280891-3112941812-1175424509-500" /></FileGroupActions></DatascreenTemplate></DatascreenTemplates><FileGroups ></FileGroups></Root>
"@
$FSRMTemplate | Out-File -FilePath C:userspublicFSRMTemplate.xml
Filescrn template import /file:C:userspublicFSRMTemplate.xml
Remove-Item -path C:UsersPublicFSRMTemplate.xml
#Creates Script Block to perform email message and block SMB Permissions. Exports script block to a PS1 for the File Screen Template.
$DenyPermissionsScript = @"
#One second delay to give script enough time to grab newest event logs
sleep -Seconds 1
#Looks in event log for the custom event message generated by the file screen audit. Input's username of the offender into a variable.
`$RansomwareEvents = get-eventlog -logname Application -message "*ransomware*" -newest 50 | where {`$_.eventid -eq 8215}
`$username = (`$RansomwareEvents.message).split()[1]
`$username = `$username -replace ".*\"
#Blocks SMB share access for user
Get-SmbShare | Where-Object currentusers -gt 0 | Block-SmbShareAccess -AccountName `$username -force
#get name of computer and domain name for email message
`$computername = Hostname
`$domain = (Get-WmiObject win32_computersystem).domain
#Send Email Report to servicedesk with information
`$client = hostname
`$messageSubject = "Server `$computername on the domain `$domain is Infected being attacked by Ransomware"
`$messagebody= "The User `$username has infected the server. They have been denied access to all file shares. Please open a ticket to disinfect their machine. Once they have been disinfected, run the following powershell command on the server `$computername to unblock the user from file shares: get-smbshare | unblock-smbshareaccess -accountname `$username -force "
`$message = New-Object System.Net.Mail.MailMessage "$EmailFrom", "$EmailTo"
`$message.Subject = `$messageSubject
`$message.IsBodyHTML = `$true
`$message.Body = `$messagebody
`$smtp = New-Object Net.Mail.SmtpClient("$smtpserver")
`$smtp.Send(`$message)
"@
#Creates file path to store block smb script that is called by the FSRM template
New-Item -Path "C:scripts" -Force -Type directory
$DenyPermissionsScript | Out-File -FilePath "C:scriptsScriptToDenyPermissions.PS1"
#unblocks the script to allow for execution
Unblock-file "C:scriptsScriptToDenyPermissions.PS1"
#find all drives that are not the C drive and create file screen for those drives. Essentially all drives except the C drive will be monitored for crypto locker files.
$disks = GET-WMIOBJECT win32_logicaldisk -filter "DriveType='3'" | Where {$_.deviceid -ne "C:"}
ForEach($disk in $disks) {
$DRIVE = $DISK.DeviceID
New-FSRMFILEScreen -path "$DRIVE" -template "RansomwareCheck"
}
restart-service "File Server Resource Manager" -force
}
}
Install-FSRMRansomware -SMTPServer InsertValidMailRelayServer -EmailTo InsertEmailToSendAlertsTo -EmailFrom InsertEmailToSendEmailFrom
How to Run the Script
Running the script is really simple. I’ve created an advanced function that includes all the parameters necessary to set up the email alerts. All we need to do is edit the parameters for the function being called at the end of the script:
Once you have inserted your own parameters, save the script. To execute the script, hold down SHIFT and RIGHT CLICK on the .ps1 file. Select COPY AS PATH:
Open up an administrative powershell prompt, type in “powershell” and paste in the path we copied, press ENTER to run the script:

The script will start to run, if the File Server Resource Manager role is not installed it will begin installing.Once the script finishes, we can look at what was done by opening up Server Manager and clicking on Tools and then selecting File Server Resource Manager:
’
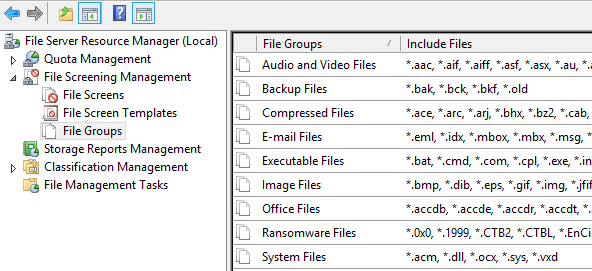
If we select the File Groups in the left window pane, we can see our newly created file group called “Ransomware files” that contains all of our known ransomware extensions to screen for:
If we select File Screen Templates in the left window pane, we can see our “RansomwareCheck” template has been created. Right click and select Edit to look at the configurations. We can see that the Ransomeware Files file group is selected:
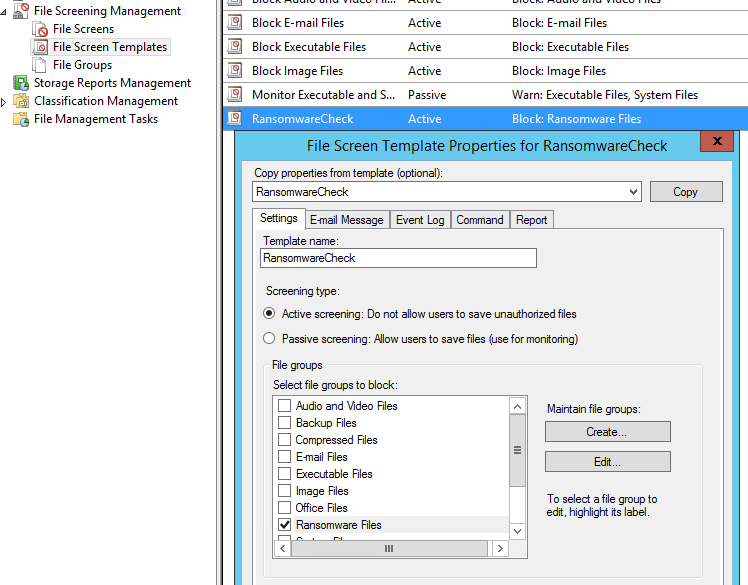
If we select the Command tab we can see that the script has been created in the C:Scripts directory on the server. This is the script that performs the SMB blocking action and sends the alert email through the email relay server specified in the script parameters:
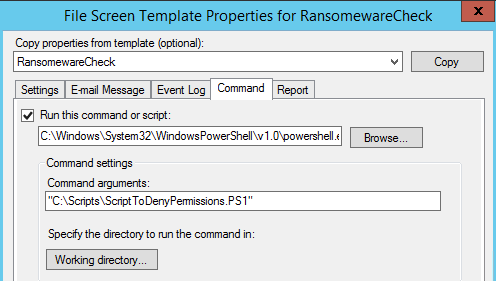
If we selec the file screens section in the left window pane, we can see that there is an active file screen on our F drive. By default the script will scan for all available volumes besides the C drive and will create a file screen for that volume. This can be manually modified if desired:
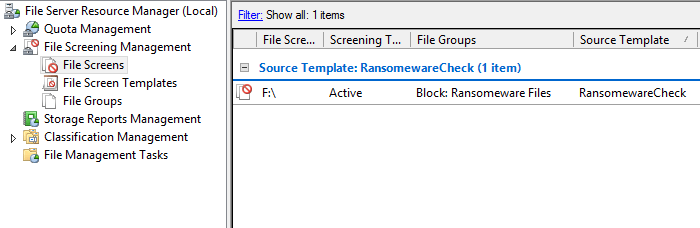
Testing the Script
If we wanted to test this out, we can go to a workstation and browse out to a shared folder on the newly configured file server. We will mimic the extension change that occurs when a file is encrypted by the cryptolocker virus by renaming the extension of a file to “.crypto”. We can see that the change gets denied:
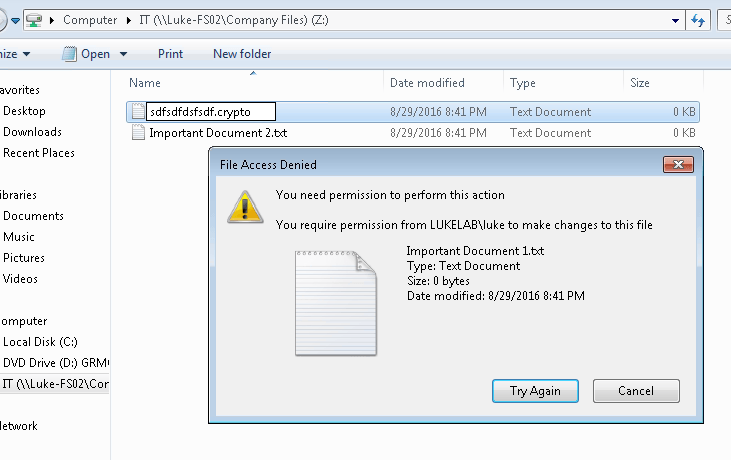
Also our user’s access to their mapped drive on the file server is now denied access:
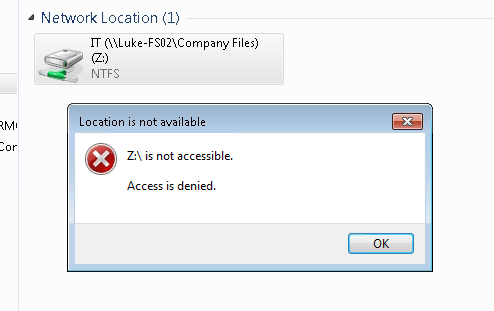
An email is then sent to the email address that we configured in the scripts parameters. We get the information on the user that was infected and the server being attacked. We also get the command that can be run to enable access once again for the user:
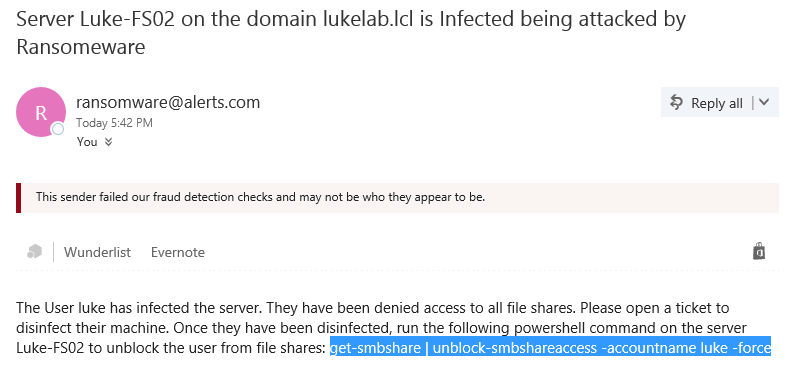
If we paste in that command into an administrative powershell prompt on the infected file server, that user can now access their shared folders again:
![]()
Keeping Updated on Known Ransomware Extensions
You will want to do your due diligence on making sure the extensions being screened are kept up to date, you can easily edit the file group and add in the extensions at any time. Tripwire has been doing an amazing job at producing security awareness posts that include the most recently discovered ransomware flavors and the extensions they use. Check out their most recent post here. This is great way to protect your organizations data by mitigating the damage done during a ransomware attack. Also, it is free which makes it even better.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









110 thoughts on "Using File Server Resource Manager to Screen for Ransomware"
Hi Luke,
Great Article, Will be implementing this across all our our 2012 servers. As our relay server listens on a non standad port and requires authentication would you be able to modify the script to accomodate this.
Many thanks
Paul
Thanks! I will modify the script to include parameters for those requirements. In the meantime, you can modify the ScriptToDenyPermissions.PS1 file that gets created. Paste the following over the “#send email report” section around line 17 and edit the values to include your own requirements:
#Send Email Report to servicedesk with information
$SMTPPort= “587”
$SMTPUsername = “username”
$SMTPPassword= “password”
$SMTPServer= “smtp.myrelay.com”
$SMTPFrom = “[email protected]”
$SMTPto = “[email protected]”
$client = hostname
$messageSubject = “Server $computername on the domain $domain is Infected being attacked by Ransomware”
$messagebody= “The User $username has infected the server. They have been denied access to all file shares. Please open a ticket to disinfect their machine. Once they have been disinfected, run the following powershell command on the server $computername to unblock the user from file shares: get-smbshare | unblock-smbshareaccess -accountname $username -force ”
$message = New-Object System.Net.Mail.MailMessage $smtpfrom, $smtpto
$message.Subject = $messageSubject
$message.IsBodyHTML = $true
$message.Body = $messagebody
$smtp = New-Object Net.Mail.SmtpClient($SMTPServer, $SMTPPort)
$SMTP.EnableSsl= $true
$smtpCreds = New-Object System.Net.NetworkCredential($SMTPUsername, $SMTPPassword)
$smtp.Send($message)
What a great resource! I just finished setting it up and am delighted with the result. I removed the line that blocked shared access–that may be too draconian for our needs. I love the notifications! Way to really help the community.
Thanks! Glad you found it useful.
First I want to thank you for this information. It will help us creating a better security against Ransomware.
I configured this solution for several of our customers. The only thing that would be nice is adding functionality to auto update the patterns, or import them from a list. For example you place a txt file on the server and a scheduled task imports de data automatically.
Can this be made to run on Windows 2008R2 servers – we don’t have any 2012’s as yet but could use this extra protection on the 2008s. Thanks!
Unfortunately no. Some of the cmdlets used in the script are native to Server 2012 and higher.
The exact script that Luke posted won’t work because it’s specific to 2012, but we have posted a 2008 R2-compatible script on our site at https://fsrm.experiant.ca which essentially does the same thing.
Thanks for the share!
Error for me!!! Help!! Sorry i don’t speak english, I from Brazil!!
Windows Server 2012
Filescrn : The term ‘Filescrn’ is not recognized as the name of a cmdlet, function, script file, or operable program.
Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At C:ScriptsInstall-FSRMRansomeware.ps1:53 char:13
Filescrn template import /file:C:userspublicFSRMTemplate.xml
~~~~~~~~
CategoryInfo : ObjectNotFound: (Filescrn:String) [], CommandNotFoundException
FullyQualifiedErrorId : CommandNotFoundException
Make sure the File Server Resource Manager role is installed on your file server. The script does the work of installing it, but it’s possible that portion was not successful.
Try running the following command in an administrative powershell console and then re-run the script:
Install-WindowsFeature fs-resource-manager
Error for me!!! Help!! Sorry i don’t speak english, I from Brazil!!
Windows Server 2012
Filescrn : The term ‘Filescrn’ is not recognized as the name of a cmdlet, function, script file, or operable program.
Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At C:ScriptsInstall-FSRMRansomeware.ps1:53 char:13
Filescrn template import /file:C:userspublicFSRMTemplate.xml
~~~~~~~~
CategoryInfo : ObjectNotFound: (Filescrn:String) [], CommandNotFoundException
FullyQualifiedErrorId : CommandNotFoundException
Legend! Thanks mate. Best solution I have found so far. I did get this error after it completed the screen for the last drive but hasn’t prevented it from working. I already had the email details set in FSRM though.
New-FSRMFILEScreen : 0x80045306, The specified path is invalid.
At C:Install-FSRMRansomeware.ps1:149 char:41
New-FSRMFILEScreen -path “$DRIVE” -temp …
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
CategoryInfo : NotSpecified: (MSFT_FSRMFileScreen:Root/Microsoft/…_FSRMFileScreen) [New-FsrmFileScree
n], CimException
FullyQualifiedErrorId : HRESULT 0x80045306,New-FsrmFileScreen
Legend! Thanks mate. Best solution I have found so far. I did get this error after it completed the screen for the last drive but hasn’t prevented it from working. I already had the email details set in FSRM though.
New-FSRMFILEScreen : 0x80045306, The specified path is invalid.
At C:Install-FSRMRansomeware.ps1:149 char:41
New-FSRMFILEScreen -path “$DRIVE” -temp …
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
CategoryInfo : NotSpecified: (MSFT_FSRMFileScreen:Root/Microsoft/…_FSRMFileScreen) [New-FsrmFileScree
n], CimException
FullyQualifiedErrorId : HRESULT 0x80045306,New-FsrmFileScreen
Hi
This is a great script and works almost perfect! I’m saying almost because I have found one problem. When I unblock user’s access to SMB and logon to the workstation and change extension of the file again, it will block the file extension change but will not block access to the share! Have anyone tested it that way and what results did you get?
For some reason the command task won’t re-trigger after its already been run. I put in a work around by adding restart-service “File Server Resource Manager” -force to the script that deny’s SMB permissions.
Have you tried changing the notification limits interval from 60 min to 0 (specifically for email, event log and command)? That should allow it to run for every attempt.
I’ll give that a try, thanks for the suggestion!
Hi
This is a great script and works almost perfect! I’m saying almost because I have found one problem. When I unblock user’s access to SMB and logon to the workstation and change extension of the file again, it will block the file extension change but will not block access to the share! Have anyone tested it that way and what results did you get?
There’s a well-maintained list of extensions and files used by many cryptolocker variants here (https://fsrm.experiant.ca/api/v1/get) in json format. There’s also a similar (but not as elegant on Windows 2012) project here (https://github.com/m-dwyer/CryptoBlocker) that contains powershell to acquire the json and split it into 4kb chunks for FSRM.
I’m going to look at combining the 2, so using your script above but downloading the file list from experiant so that I can schedule it to stay up-to-date with new variants, just thought I@d mention it in case you want to incorporate this yourself. The last infection I dealt with would have been caught by the experiant list but not this one.
Hi Jim,
I am looking at exactly the same thing. This script is certainly more elegant – but the extension list is minimal. A constantly updating script sourcing the extension repository is all it needs to really make this work well. I realise I am a bit late to the party on this one – did you manage to achive this aim at all, and if so would you be willing to share your findings?
Thanks to Luke for the work done on this.
A lot of people are recommending to look at the list published on experiant’s API: https://fsrm.experiant.ca/api/v1/get it has a very complete and updated list. Since it’s an API, PowerShell can be used to reference this list in a very efficient manner.
I know this thread is three years stale but I found a slight bug and I think others might benefit from the fix. This has to do with creating the $DenyPermissionsScript variable that gets written to a file. The very last line is
`restart-service “File Server Resource Manager” -force
See that backtick at the beginning of the line? What actually gets written to the file is “estart-service”. That’s the bug. Get rid of the tick and “restart-service” is correctly rendered.
Finally a huge Thank You to Luke O for writing this article and give me a jumping off point.
I was so inspired by Luke’s original script that I wrote a brand new script that achieves the same goals but uses Windows 2012 PowerShell cmdlets and works with Experiant’s well maintained list of ransomware filespecs. The script also implements honey traps to try and catch zero-day ransomware behavior. I also have a few Python scripts that will help scan your existing systems for any sign of ransomware. Without exageration, it will scan a system with 2.5 million files in about 2 minutes and 10 seconds using VoidTools Everything Search. I hope you’ll take a look and contribute at:
https://github.com/SparkyzCodez/FSRM-Anti-ransomware
This is awesome to hear! I’m glad someone was able to take this a step further and turn it into a github project. This is a great value add to the community!
I have a 2016 general file server cluster and a 2016 SOFS cluster. Is your script supported to run on those systems? Would I copy the script to the same location on both nodes so that whichever one is active, FSRM will be able to find the script to send alerts?
Yes, I have confirmed this script will work with Server 2016. It should work with a SOFS as well as long as the block permissions script is located on each server.
Hi Luke,
The command is still not triggering as what Dariusz has mentioned above, even after you have added the workaround.
Which means SMB access is still not blocked.
Deny rename is working though.
Any idea with regards to this?
I have updated the script to include no Notification limits. This allows the triggers to work every time. Let me know if it’s still not working for you. Thanks!
hi; good job and man thanks
can i apply active screen on C: Or C:windows ??
windows 20008R2
You could modify line 149 to include C: by removing | Where {$_.deviceid -ne “C:”} from that line. However, this script will only work on Server 2012 and higher since it requires PowerShell cmdlets that are native to that OS.
Hi! I see you tried to fix the issue with blocking smbshare only happening once by adding a restart of the service which WORKS but… your script leaves out the letter ‘r’ in the word ‘restart’. Add that and it’s good to go!
Good catch! Thanks!
I prefer to block all filetypes and add in tge ones I trust:
https://the-server.ninja/2016/09/06/defeat-ransomware-use-microsoft-file-server-resource-manager-fsrm-with-a-twist/
File or application whitelisting is starting to become a more common approach. It is much more secure but the trade off is accessibility and maintenance on the list of approved extension types.
anyone else has an issue as for the script needs to runs twice for it to work?
if i delete the logs from windows and test it changing the extension it does not block the user and when it email it says User was infected but if again i change the extension it works, whats worst is that if another user on another computer changes the extension it blocks and email alert saying it was the previous one rather then the one that got infected. Anyone else has had this issue?
The script has been updated to resolve this issue. There was a limit set on the notifications that was causing this.
Hi Luke,
Very nice script, thanks a stack it works a treat on Server 2012 R2 but I’m having problems with the ‘ScriptToDenyPermissions” in Server 2016?
Essentially the’ScriptToDenyPermissions’ is not correctly identifying the $username variable so this variable is not being fed into any actions that require the $username variable.
Have you by any chance tested this on Server 2016 yet?
I did confirm that this script works with Server 2016. There may be a formatting issue with the username. Try running this snippet on the server and see what $username is set to:
$RansomwareEvents = get-eventlog -logname Application -message “*ransomware*” -newest 50 | where {`$_.eventid -eq 8215}
$username = (`$RansomwareEvents.message).split()[1]
$username = `$username -replace “.*\”
$username
I think using “crypto canary” is more efficient especially because you are not having to update the file extensions frequently. I’ve also had some concerns about the read write lag of the file server having to check the file extensions against the list every time a file is saved or modified. In our environment, that has not worked well.
First I want to thank you for this information. It will help us creating a better security against Ransomware.
I configured this solution for several of our customers. The only thing that would be nice is adding functionality to auto update the patterns, or import them from a list. For example you place a txt file on the server and a scheduled task imports de data automatically.
Many people have recommended using experiant’s API to reference as a source. You could incorporate invoke-webrequest to collect the list of known extensions from https://fsrm.experiant.ca/api/v1/get.
Really awesome script, just have one tiny problem for the smb block i have been trying to test it out and no luck, I would get error on line 7 character 41 and on line 11 character 124 which one says cannot call upon expression with value NULL and the other error says cannot validate argument “account name”
Thank you
Just wanted to be more specific on the error
these are the lines that are giving the issue the rest is fine
PS C:UsersAdministrator> $username = ($RansomwareEvents.message).split()[1]
You cannot call a method on a null-valued expression.
At line:1 char:1
$username = ($RansomwareEvents.message).split()[1]
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
CategoryInfo : InvalidOperation: (:) [], RuntimeException
FullyQualifiedErrorId : InvokeMethodOnNull
PS C:UsersAdministrator> Get-SmbShare | Where-Object currentusers -gt 0 | Block-SmbShareAccess -AccountName $username -force
Block-SmbShareAccess : Cannot validate argument on parameter ‘AccountName’. The argument is null or empty. Provide an argument that is not null or empty, and
then try the command again.
At line:1 char:84
… s -AccountName $username -force
~~~~~~~~~
CategoryInfo : InvalidData: (:) [Block-SmbShareAccess], ParameterBindingValidationException
FullyQualifiedErrorId : ParameterArgumentValidationError,Block-SmbShareAccess
What version of windows server are you running this on?
Hi Luke,
Thanks for the info when I try to run the script nothing happens powershell just drops back to the prompt, don’t get an error, I am sure it is something I am doing wrong, I copied everything in the script above until notepad.
Thanks,
Craig
Try to copy the script into an Administrative PowerShell ISE. Then make your edits and run the script, see if that works for you.
Sorry have installed the script now and done a test which worked, but 2nd time I tested it although I couldn’t rename the file it didn’t block me or send the email ?
Try running this to set the notification levels to 0 per Doug Glasgow’s findings it should allow for multiple triggers: Set-FsrmSetting -EmailNotificationLimit 0 -EventNotificationLimit 0 -CommandNotificationLimit 0 -ReportNotificationLimit 0
I’ll try to get this added to the script. Thanks!
The ressource manager is a bit slow isn’t it?
user 1 is changing a file extension to a cryptolocker extension. -> getting an email, log entry, can not change the filename and the user is getting blocked.
about 1 minute later user 2 is changing a file extension to a cryptolocker extension. -> getting no email, no log entry, is not getting blocked, but he can not change the filename.
The solution is definitely at the mercy of the limitations of resource manager. However, this works as a great free “safety net” that people can use to protect themselves from potential havoc on their environment. In the case were multiple users receive the same email and click on the attachment, the notification email would hopefully provide awareness where IT operations can catch it before it encrypts too many files.
i was playing around a little bit and found out, that if the ressource manager blocks a user from changing a file, i have to reset the “start task as” to “system” in the comand tab. Then it works a second time.
Try running this to set the notification levels to 0 per Doug Glasgow’s findings it should allow for multiple triggers: Set-FsrmSetting -EmailNotificationLimit 0 -EventNotificationLimit 0 -CommandNotificationLimit 0 -ReportNotificationLimit 0
Hi there,
Where can I get an update list of ransomware extensions?
Thanks!
Hi John,
A lot of people recommend the list form experiant. This is in JSON format and easy to automate against: https://fsrm.experiant.ca/api/v1/get.
Here is a site that updates the extensions also https://fsrm.experiant.ca/
On Github they have a script https://github.com/m-dwyer/CryptoBlocker
that does pull from the site but you need to modify the script so it breaks the File Group length into multiple groups. Also if you rerun the script it will remove existing exclusions and any custom email message. Maybe you can modify your script with this to get the perfect script. Only downside is that if that person whom owns frsm.experiant.ca adds good extensions like *.doc that will cause a lot of pain. Wondering if there is a way to have the script update from a text file that you can keep updating your self.
That is a great point, the experian API could potentially break an environment. You could edit line 42 and put in something like this to collect the extensions from a text file: New-FsrmFileGroup -name “Ransomware Files” -IncludePattern (get-content c:cryptoexts.txt)
Luke,
Thanks for the script.
I executed the same script on my environment but the file server resource manger is not installating automatically from script.
Regards,
Varma.
What error do you get when running Install-WindowsFeature fs-resource-manager in a PowerShell console on that server?
There’s a well-maintained list of extensions and files used by many cryptolocker variants here (https://fsrm.experiant.ca/api/v1/get) in json format. There’s also a similar (but not as elegant on Windows 2012) project here (https://github.com/m-dwyer/CryptoBlocker) that contains powershell to acquire the json and split it into 4kb chunks for FSRM.
I’m going to look at combining the 2, so using your script above but downloading the file list from experiant so that I can schedule it to stay up-to-date with new variants, just thought I@d mention it in case you want to incorporate this yourself. The last infection I dealt with would have been caught by the experiant list but not this one.
Thanks for the share! I’m glad to hear people are using this as a base to make their own. I really like the experiant API and think it make’s perfect sense to integrate it into this script.
First of all thanks for the work on this. I have been trying to set this up using different scripts and found yours today after the most I could get was an alert and not locking the user out.
The ScriptToDenyPermissions works, but only if I run it after trying to save a test file. What do I need to do to have it alert and lock the share for the user when they attempt to save a “bad” file to the share?
If you set up file screening on the share, it will allow you to detect certain flagged extensions that you can use to trigger the ScriptToDenyPermissions.
Hi Luke,
Thanks a lot for the script 🙂 I’m going to give it a bash. Are you aware of an updated ransomware file extension list or point me in the right direction?
Kind Regards