Save to My DOJO
One of the great things about the Hyper-V virtual switch is that it can be used to very effectively isolate your virtual machines from the physical network. This grants them a layer of protection that’s nearly unparalleled. Like any security measure, this can be a double-edged sword. Oftentimes, these isolated guests still need some measure of access to the outside world, or they at least need to have access to a system that can perform such access on their behalf.
There are a few ways to facilitate this sort of connection. The biggest buzzword-friendly solution today is network virtualization, but that currently requires additional software (usually System Center VMM) and a not-unsubstantial degree of additional know-how. For most small, and even many medium-sized organizations, this is an unwelcome burden not only in terms of financial expense, but also in training/education and maintenance.
A simpler solution that’s more suited to smaller and less complicated networks is software routing. Because we’re talking about isolation using a Hyper-V internal or private switch, such software would need to be inside a virtual machine on the same Hyper-V host as the isolated guests.
If you’re not clear on how this would work, you can refer to one of our articles on the Hyper-V virtual switch. This is the same image that I used in that article:
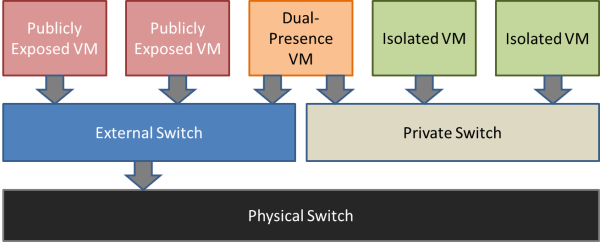
External and Private Switch
The routing VM would be represented in that image as the Dual-Presence VM.
Choosing a Software Router
There are major commercial software routing solutions available, such as Vyatta. There are free routing software packages available, such as VyOS, the community fork for Vyatta. These are all Linux-based, and as such, are not within my scope of expertise. However, it should be possible to deploy them as Hyper-V guests.
What we’re going to look at in this article is Microsoft’s Routing and Remote Access Service. It’s an included component of Windows Server, and it’s highly recommended that an RRAS system perform no other functions. If you have a spare virtualization right, then this environment is free for you. Otherwise, you’ll need to purchase an additional Windows Server license.
Do not enable RRAS in Hyper-V’s management operating system! Doing so does not absolve you of the requirement to provide a virtualization right and networking performance of both the management operating system and RAS will be degraded. It’s also an unsupported configuration. To make matters worse, the performance will be unpredictable.
Step 1: Build the Virtual Machine
Sizing a software router depends heavily upon the quantity of traffic that it’s going to be dealing with. However, systems administrators that don’t work with physical routers very often are usually surprised at just how few hardware resources are in even some of the major physical devices. My starting recommendation for the routing virtual machine is as follows:
- vCPUs: 2
- Dynamic Memory: 512MB Startup
- Dynamic Memory: 256MB Minimum
- Dynamic Memory: 2GB Maximum
- Disk: 1 VHDX, Dynamically Expanding, 80GB (expect < 20 GB use, fairly stagnant growth)
- vNIC: 1 to connect to the external switch
- vNIC: 1 per private subnet per private/internal switch (wait on this during initial build)
- OS: latest Windows Server that you are licensed for
- This VM won’t necessarily need to be a member of your domain. If it’s going to be sitting in the perimeter, then you might consider leaving it out. Another option is to leave it in the domain but with higher-than-usual security settings. A great thing to do for machines such as this is disable cached credentials, whether it’s left in the domain or not.
Once the virtual machine is deployed, monitor it for CPU contention, high memory usage, and long network queue lengths. Adjust provisioning upward as necessary.
During VM setup, I would only create a single virtual adapter to start, and place it on the external virtual switch. Then use PowerShell to rename that adapter:
Get-VMNetworkAdapter –VMName svrras | Rename-VMNetworkAdapter –NewName External
Then, boot up the virtual machine and install Windows Server (I’ll be using 2012 R2 for this article). Rename the adapter inside Windows Server as well to reflect that it connects to the outside world. These steps will help you avoid a lot of issues later. If you’ve already created your adapters and would like a way to identify them, you can disconnect them from their switches and watch which show as being unplugged in the virtual machine.
Before proceeding, ensure you have added all virtual adapters necessary, one for each switch. The virtual adapter connected to the external virtual switch is the only one that requires complete IP information. It should have a default gateway pointing to the next external hop and it should know about DNS servers. It can use any IP on that network that you have available. It only needs a memorable IP if other systems will need to be able to send traffic directly to hosts on the isolated network.
All other adapters require only an IP and a subnet mask. The IP that you choose will be used as the default gateway for all other systems on that switch, so you’ll probably want it to be something easy to remember. If you’re using the router’s operating system as a domain member or in some other situation in which it will be able to register its IP addresses in DNS, make sure that you disable DNS registration for all adapters other than the one that’s in the primary network.
For reference, my test configuration is as follows:
- System name: SVRRAS
- “External” adapter: IP: 192.168.25.254, Mask: 255.255.255.0, GW 192.168.25.1
- “Isolated” adapter: IP: 172.16.0.1, Mask: 255.255.0.0, GW: None
In order for this to work, you’ll need to make some adjustments to the Windows Firewall. If you want, you can just turn it off entirely. However, it is a moderately effective barrier and better than nothing. We’ll follow up on the firewall after the RRAS configuration explanation.
Step 2: Installing and Configuring RRAS
Once Windows is installed and you have all the necessary network adapters connected to their respective virtual switches, the next thing to do is install RRAS. This is done through the Add Roles and Features wizard, just like any other Windows Server role. Choose Remote Access on the Roles screen:
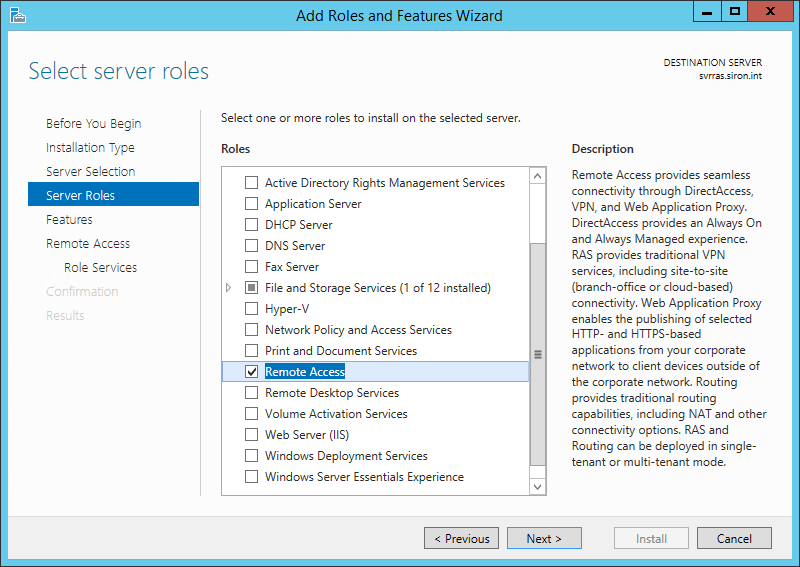
RRAS Server Role
On the Role Services screen, check the box for Routing. You’ll be prompted to add several other items in order to fully enable routing, which will include DirectAcccess and VPN (RAS) on the same screen:
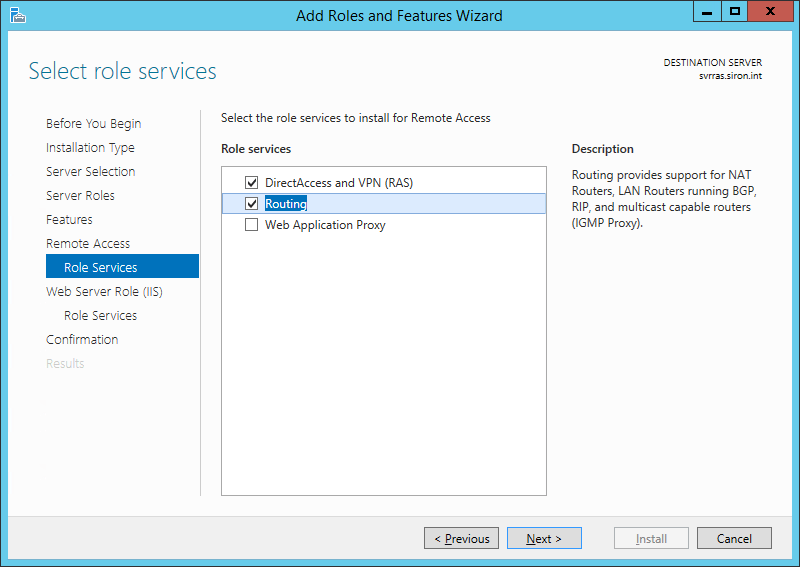
RRAS Role Services
After this, just proceed through, accepting the suggested settings.
Once the installation is complete, a reboot is unnecessary. You just need to configure the router. Open up the Start menu, and find the Routing and Remote Access snap-in. Open that up, and you’ll find something similar to the following screenshot. Right-click on your server’s name and click Configure and Enable Routing and Remote Access.
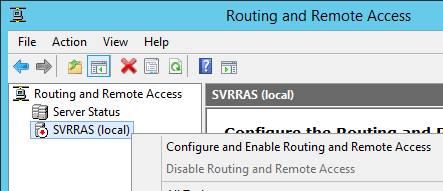
Configure RRAS
On the next screen, you have one of two choices for our purposes. The first is Network Address Translation (NAT). This mode works like a home Internet router does. All the virtual machines behind the router will appear to have the same IP address. This is a great solution for isolation purposes. It’s also useful when you haven’t got a hardware router available and want to connect your virtual machines into another network, such as the Internet. Your second choice is to select Custom configuration. This mode allows you to build a standard router, in which the virtual machines on the private network can be reached from other virtual machines by using their IP addresses. I won’t be illustrating this method as it doesn’t do a great deal for isolation.
On the next screen, you’ll tell the routing system which of the adapters is connected to the external network:
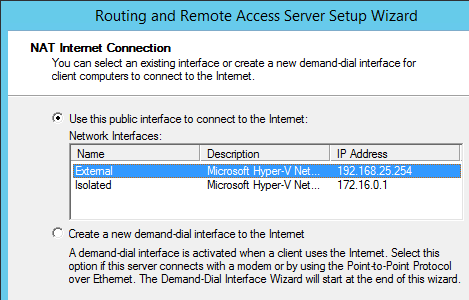
RRAS Adapter Selection
On the next screen, you’ll choose how addressing is handled on the private networks. The first option will set up your RRAS system to perform DHCP services for them and forward their DNS requests out to the DNS server(s) you specified for the external network. If you choose the second option, you can build your own addressing services as desired. I’m just going to work with the first option for the sake of ease (and a quicker article):
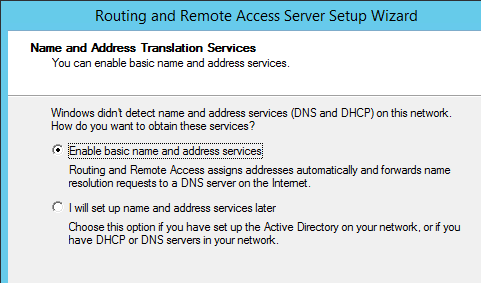
RRAS Name Services
Once this wizard completes, you’ll be returned to the main RRAS screen where the server should now show online (with a small upward pointing green arrow). That’s really all it takes to configure RRAS inside a Hyper-V guest.
Step 3: Configure the Virtual Machines
This is probably the best part: there is no necessary configuration at all. Just attach the virtual machines to the private switch and leave them in the default networking configuration. Here’s a screenshot from a Windows 7 virtual machine I connected to my test isolated switch:
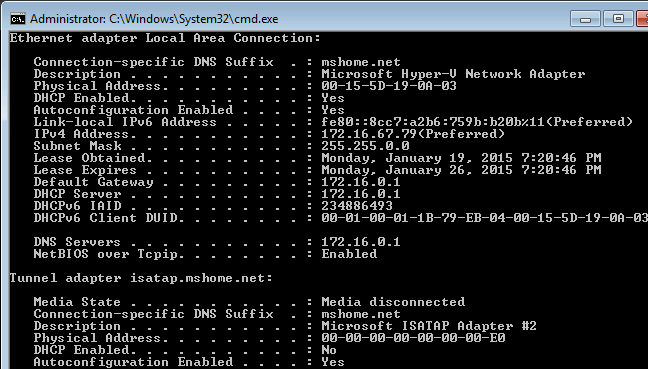
RRAS in a VM: Demo
You’ll see that it’s using the IP information of SVRRAS’s adapter on the isolated switch for DHCP, gateway, and DNS information. As long as the firewall is down or properly set on the RRAS system, it will be able to communicate as expected.
[optin-monster-shortcode id=”gaua0qrhzreh818c”]
Windows Firewall on the RRAS System
The easiest thing to do with the Windows Firewall is to just turn it off. If you’re using it at the perimeter, that’s a pretty bad idea. While it may not be the best firewall available, it does pretty well for a software firewall and seems to have the fewest negative side effects in that genre.
For many, a build of this kind exposes them to a completely new configuration style, one that many hardware firewall administrators have dealt with for a very long time. In a traditional software firewall build running on a single system, you usually only have to worry about inbound and outbound traffic on a single adapter. Now, you have to worry about it on at least two adapters. This is a visualization:
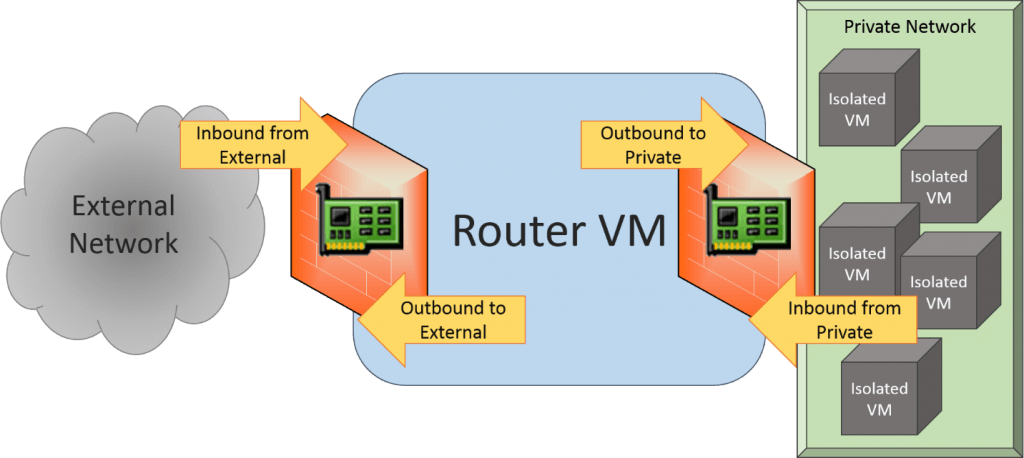
RRAS and Windows Firewall
When configuring Windows Firewall, you have to be mindful of how this will work. In order to allow guests on the private network to access web sites on the external network, you’ll need to open port 80 INBOUND on the adapter connected to the private network. This kind of management can get tedious, but it’s very effective if you want to further isolate those guests.
What you might want to do instead is leave the firewall on that connects to the external network but disable it for the private network. Then, your private guests will have receive the default levels of protection from the router VM’s firewall. You could then turn off the firewalls in the guests, if you like. In order to do this, open up Windows Firewall with Advanced Security on the router VM (or target the MMC from a remote computer). In the center pane, click Windows Firewall Properties or, in the left pane, right-click Windows Firewall with Advanced Security and click Properties. Next to Protected network connections, click Customize. In the dialog that appears, uncheck the box that represents the network adapter on the private switch. Click OK all the way out. I’ve renamed my adapters to “Isolated” and “External for the following screenshot:
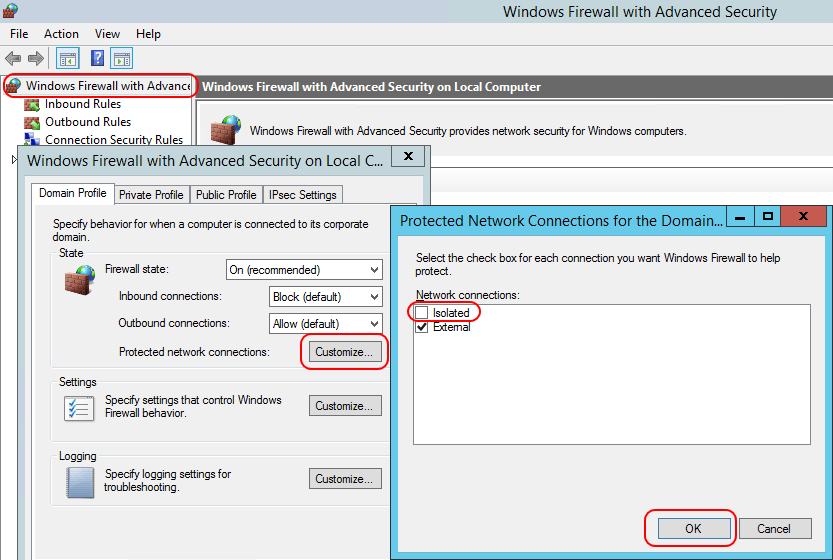
RRAS Firewall Adapter Selection
DMZs and Port Forwarding in RRAS
You might want to selectively expose some of your guests on the private network to inbound traffic from the external network. Personally, I don’t see much value in using the DMZ mode. It’s functionally equivalent and less computationally expensive to just connect a “DMZ” virtual machine directly to the external switch and not have it go through a routing VM at all. Port forwarding (sometimes called “pincushioning”), on the other hand, does have its uses.
Open the Routing and Remote Access console. Expand your server, then expand the IP version (IPv4 or IPv6) that you want to configure forwarding for. Click NAT. In the center pane, locate the interface that is connected to the external switch. Right-click it and click Properties.
If you wish to configure one or more “DMZ” virtual machines, the Address Pool tab is where this is done. First, you create a pool that contains the IP address(es) that you want to map to the private VM(s). For instance, if you want to make 192.168.25.78 the IP address of a private VM, then you would enter that IP address with a subnet mask of 255.255.255.255. Once you have your range(s) configured, you use the Reservations button to map the external address(es) to the private VMs address(es).
For port forwarding, go to the Services and Ports tab. If you check one of the existing boxes, it will present you with a prefilled dialog where all you need to enter is the IP address of the private VM for which you wish to forward traffic:
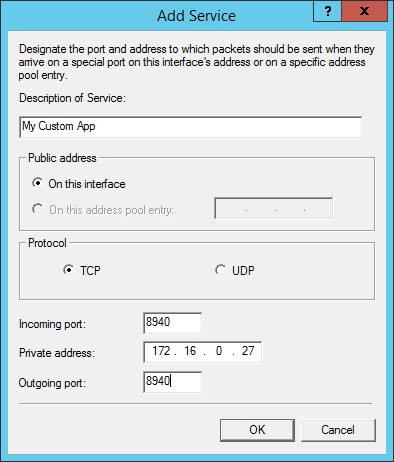
RRAS Port Forwarding
In this screenshot, the On this address pool entry field is unavailable. That’s because I did not add any other IP addresses on the Address Pool tab. If you do that, then the external adapter will have multiple IPs assigned to it. If you don’t use those additional IPs for DMZ purposes, then you can use them here. The reason for doing so is so that multiple private virtual machines can have port forwarding for the same service. One use case for doing so is if you have two or more virtual machines on your private switch serving web pages and you want to make them all visible to computers on the external network.
VLANs and RRAS
This is a topic that comes up often. If you’ve read our networking series, then hopefully you already know how this works. VLANs are a layer 2 concept while routing is layer 3. Therefore, VLAN assignments for virtual machines on your private virtual switch will have no relation to any other VLANs anywhere else. Using VLANs on the private switch is probably not useful unless you need to isolate them from each other. If that’s the case, then you’ll need to make a distinct virtual adapter inside the routing virtual machine for each of those VLANs, or it won’t be able to communicate with the other guests on that VLAN.
Happy Routing
That’s really all there is to getting routing working through a Hyper-V virtual machine. This is a great solution for isolating virtual machines and for test labs.
Do remember that it’s not as efficient or as robust as using a true hardware router.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!









230 thoughts on "How to Install and Configure TCP/IP Routing in a Hyper-V Guest"
Hello Mr. Siron,
thank you for sharing your know how.
I’m trying to build my home Lab including a domain controller. The so built Domain should be reachable by computer that are not directly connected to may home isp router hrough WLAN or LAN.
I have a question regarding the Network built below: is there any possibility to make the use your solution describe above for my ppurpose please. Which configuration should I eventually apply to the virtual DNS,physical DNS(router) and others virtual client please.
Thanks in Advance.
I don’t know if you intended to include some sort of diagram, but I don’t see anything.
Routing is routing. Once you have the networks and software router in place, you don’t configure it any differently than you would a physically routed environment.
Hello Mr. Siron,
thank you for sharing your know how.
I’m trying to build my home Lab including a domain controller. The so built Domain should be reachable by computer that are not directly connected to may home isp router hrough WLAN or LAN.
I have a question regarding the Network built below: is there any possibility to make the use your solution describe above for my ppurpose please. Which configuration should I eventually apply to the virtual DNS,physical DNS(router) and others virtual client please.
Thanks in Advance.
Eric,
Thanks for your blog! I’m trying to setup your configuration, but take it to the next level. I’m trying to have the dual presence and multiple private subnets running individual RRAS servers tied to the main dual presence. I can get everyone to go out but can’t get ports to route to individual subnets.
Main dual presence: 192.168.0.x external
192.168.1.x. internal
Private 1 192.168.1.x external
172.16.10.x internal
Private 2 192.168.1.x external
172.16.20.x internal
All internal subnets can go to the cloud but can’t route ports like 3389 into the private networks (clients). I have NAT and Routing on all RRAS servers and firewall turned off. I’m forwarding ports to the external interface of the private RRAS then from the private RRAS to the client. Also don’t have any IP pools setup.
Thanks
That’s pretty elaborate, but I can’t think of any reason why it wouldn’t work. Did you test the intermediate steps first? As in, do you know that the port is hitting each subsequent point of translation? Wireshark is probably what you’re going to need to sort this out.
Eric,
Thanks for your blog! I’m trying to setup your configuration, but take it to the next level. I’m trying to have the dual presence and multiple private subnets running individual RRAS servers tied to the main dual presence. I can get everyone to go out but can’t get ports to route to individual subnets.
Main dual presence: 192.168.0.x external
192.168.1.x. internal
Private 1 192.168.1.x external
172.16.10.x internal
Private 2 192.168.1.x external
172.16.20.x internal
All internal subnets can go to the cloud but can’t route ports like 3389 into the private networks (clients). I have NAT and Routing on all RRAS servers and firewall turned off. I’m forwarding ports to the external interface of the private RRAS then from the private RRAS to the client. Also don’t have any IP pools setup.
Thanks
Hi Eric, i’ve setup successfully an environment with your instructions, but i setup as internal rather than private to be able to RDP the VMs by name, and use the internal DNS. Wonder if i did right?
can’t send visio, but i did :
Router VM is 10.10.0.254, Internal DC/DNS/DHCP is 10.10.0.1
– i setup an internal adapter on the host, giving it 10.10.0.2 with a gateway to the router and a dns suffix of sp2013.local (my test domain), hopefully routing only internal traffic thru it 🙂
– on the router VM, i setup internal as 10.10.0.254 and DNS = 10.10.0.1 external as automatic DHCP DNS
– on the Internal DC, i setup 10.10.0.1, gateway 10.10.0.254
is this ok?
From your description, it sounds OK. But, I’m a little confused on where the Hyper-V Server is in this mix. This 10.10.0.0 network is all internal and going through the router VM, and the router VM is the only system with anything on an external switch? If that’s how you did it, then everything looks OK.
Don’t forget to use tools like Wireshark to see how your traffic is moving.
Hi Eric, i’ve setup successfully an environment with your instructions, but i setup as internal rather than private to be able to RDP the VMs by name, and use the internal DNS. Wonder if i did right?
can’t send visio, but i did :
Router VM is 10.10.0.254, Internal DC/DNS/DHCP is 10.10.0.1
– i setup an internal adapter on the host, giving it 10.10.0.2 with a gateway to the router and a dns suffix of sp2013.local (my test domain), hopefully routing only internal traffic thru it 🙂
– on the router VM, i setup internal as 10.10.0.254 and DNS = 10.10.0.1 external as automatic DHCP DNS
– on the Internal DC, i setup 10.10.0.1, gateway 10.10.0.254
is this ok?
Im trying to to build a hyper v lab in our office for test purposes.
So i have installed VMware Workstation 9 to setup Win server 2012 (host) and from the host i created 1 (VM) guest. Im on thre process of configuring DHCP in hyper V but not pretty sure what would be the IP address configuration in virtual switch based on my lab set up.
I need some insights on how to setup dhcp in a hyper v environment. I have already Internal virtual switch assigned to my VM guest.
Don’t over think it. The Hyper-V virtual switch is purely layer 2. Except for 802.1q processing, it’s about as smart as a cheap 8-port switch you’d pick up in a retail store. It doesn’t do anything with IP addresses.
I’m not 100% clear on your design but the easiest way to approach it is to imagine what it would be like if you were just using physical switches. Set up your DHCP environment like that.
If you’re asking if you can make Hyper-V do DHCP, you can’t. You can install the DHCP server role in Windows Server 2012. I’ve seen some people use Internet Connection Sharing.
Im trying to to build a hyper v lab in our office for test purposes.
So i have installed VMware Workstation 9 to setup Win server 2012 (host) and from the host i created 1 (VM) guest. Im on thre process of configuring DHCP in hyper V but not pretty sure what would be the IP address configuration in virtual switch based on my lab set up.
I need some insights on how to setup dhcp in a hyper v environment. I have already Internal virtual switch assigned to my VM guest.
Excellent post. I had to point the isolated VMs to the internal DNS address (to the DC/DNS server in my test isolated domain) and point it to an external DNS to get DNS queries to work for both internal and external addresses, and I chose to set up name and address services later, and it works perfectly.
Thumbs up!
Excellent post. I had to point the isolated VMs to the internal DNS address (to the DC/DNS server in my test isolated domain) and point it to an external DNS to get DNS queries to work for both internal and external addresses, and I chose to set up name and address services later, and it works perfectly.
Thumbs up!
Thank you for this How-To Eric, it took me a lot of hunting to finally find what i was looking for and your explanation was simple, accurate and worked a treat. I don’t have a windows background but I know networks fairly well and it frustrated me hunting for “Windows Server Gateway” that apparently did what I needed. So after learning how to configure the DHCP I needed the NATing to work. Piece of cake with Linux 🙂 but i needed a microsoft solution.
Thanks heaps.
Thank you for this How-To Eric, it took me a lot of hunting to finally find what i was looking for and your explanation was simple, accurate and worked a treat. I don’t have a windows background but I know networks fairly well and it frustrated me hunting for “Windows Server Gateway” that apparently did what I needed. So after learning how to configure the DHCP I needed the NATing to work. Piece of cake with Linux 🙂 but i needed a microsoft solution.
Thanks heaps.
I know this is an old article but I am hoping you can help me. Lets say I have my setup exactly like you describe for the VM RaaS server. I have 3 other VMs as well, an Essentials 2016 Server, a Server 2016 Web server, and a Server 2016 Exchange server. I used to have all three VMs connected to the same “External” switch so each VM could access the internet semi-directly (I think they were going through the essentials server?). Well, from my workstation (a separate computer all-together but on the same router as the VM Host) I used to connect to each individual server using remote desktop. Obviously, now my workstation doesn’t see any of the servers aside from the RaaS VM and the VM Host. Whats the best way to allow remote desktop again to each server? I mean, obviously I can setup port forwarding to the web server to allow web access, and I can forward the mail ports to the exchange server, and I can forward specific ports to the Essentials server as needed as well. But, when I need to get to each server using RDS, they all use the same port for remote desktop so I cant setup port forwarding when its all three servers. On the internal servers, would I change the port for RDS and then connect to each server (from the workstation) using a different port? If so, from RDS on the workstation, instead of putting “Exchange-Server” as the computer name, would I put the RaaS server ip with the port number attached? Like “192.168.0.1:3386” etc? There has to be a better way.
Sorry for the response delay, I wasn’t getting notifications.
Yes, you would have to configure Remote Desktop Services on each system to use a port other than 3389 and forward in the RRAS system. Alternatively, you would need to configure RRAS to use standard routing rather than NAT, but it doesn’t sound like you need that.
In fact, it sounds like you already had an external router somewhere in your system, though, so, other than this headache, I’m not sure what RRAS gives you that you didn’t already have.
Hi Eric,
PLEASE HEEELP!!
I am a total Newbie and my host is Windows 10 with Hyper V activated. I have only one NIC and I would like to set up a lab where I can have a Domain Controller is using it’s own AD DNS and DHCP. Supporting at least two subnets that communicate with Server replication and Internet access also maybe one subnet private. Is your set up the right one for me?
If you’re as new as you are implying, that’s an awful lot to take on in one go. Yes, it can work. You’ll need to have a fairly decent understanding of TCP/IP layer 2 and layer 3 operations for a smooth experience.
Hi All,
I am trying to build a home lab on my laptop for testing purpose.
This the link to the diagram: https://drive.google.com/open?id=17ssUcXqJ9ZJwe0w8pYHaYcW1F8kUNybQ
Objectives to be achieved: (1) All the nested VMs in VM1shall have internet assess. (2) The nested VMs in VM1 can ping the VM2 and vice versa (i.e. VM2 and ping all nested VMs in VM1)
Anyone have a solution to this?
Hi Eric!
I want to setup a Linux VM especially for Seafile. ATM I’m using Ubuntu Server 18.04 LTS and have successfully done a connection over SSH to my VM. But now I want to update some packages via apt-get but can’t. I already routed port 80, 443 and 21 to the VM but can’t update anyway. I followed your tutorial clearly but I stuck now. Do you maybe have some hints for me?
Hyper-V is running on a Windows Server 2012 R2 Standard.
Many thanks!
Best regards,
Johannes
I don’t understand how routing those ports into the VM would help the VM to communicate outward. As long as the VM is connected to a functioning external switch, it’s all TCP/IP from there.
HI all,
i’m running into an issue where my hyper-V host and my VM managing RRAS can acces both networks (internal and external) but the clients using my RRAS as gateway cannot use the external link:
– hyper-v has two NIC, 192.168.8.240/24 connected to a 4G box, 10.14.254.6/24 connected to our intranet through a MPLS
– the VM RRAS has 10.14.254.5 and 192.168.8.241 as IP
– the VM is our Gateway
– the lowest gateway metric is associated to our internal NIC so i can get AD / DNS connectvity at all time without specific rules
as soon as i define an internet static route in the RRAS mmc (let’s say 8.8.8.8), both the Hyper-v host and the VM can use this route to access google dns
The client won’t use the internal nic anymore but the tracert stops rights after the RRAS VM and roams around until 30 hops and nothing.
any idea where i forgot something ?
Why is Hyper-V multi-homed? I don’t see what that does for you. It should also connect out via the RRAS VM.
Have you verified that Hyper-V is accessing the new route via RRAS? It doesn’t make sense for the host to be able to use it and not any other client. I’m assuming there’s some minor problem with the route configuration, but it should impact everyone besides the RRAS VM, not work for some but not others.
Thnaks Eric for quick reply,
Hyper-V is multi homed because i need to offer 2 distinct NIC to my VM, no ?
one NIC for “high speed” internet from 4G and one NIC for “low speed” intranet
the hyper-v has the RRAS as gateway too and use the RRAS to bind to the external nic for internet acces.
if i do not create any routing rules, everyone use the internal nic to acces internet and intranet.
as soon as i create a routing rule for let’s say tracert 8.8.8.8, VM and hyper-v host use the external link and it works. clients on the network use the external link too but tracert fails.
the resultant command i add is :
add route 8.0.0.0 mask 255.0.0.0 192.168.8.1 IF 2 -p
192.168.8.1 is the gateway and the 4G router
#2 is the interface number of my second VM card for internet
FYI : i do not use RA at all, just routing
the 4G router takes care or NAT
Adapters, especially IPs, in the management OS have no relationship with the adapters in guest VMs. When you give a guest VM a virtual adapter, that’s its network connection. You only need to provide physical access via the management OS, not layer 3. Get rid of the 10.14.254.6 address at least. I’d have to see your entire networking configuration to tell you exactly how far to delete, but definitely get rid of that IP. If it’s on a virtual NIC, delete the vNIC.
I have to confess that I have not done RRAS for a very, very long time. Probably not since a few months after writing this article. Don’t you have to create those static routes in the RRAS console? Isn’t “add route” only for the local system?
Hi,
Just found this excellent post when playing with nested Hyper-V VMs within Azure. If I understand correctly, in order to isolate VMs but still providing controlled access to the outside world, a dual presence VM provides traffic “routing” by using RRAS. Only is the NAT function of RRAS used in this scenario. In that case, can we just create a NAT object to perform the same function, without installing RRAS?
In the example of the post, the dual-presence router VM host, SVRRAS, have the following IP configuration:
• “External” adapter: IP: 192.168.25.254, Mask: 255.255.255.0, GW: 192.168.25.1, DNS: 168.63.129.16
• “Isolated” adapter: IP: 172.16.0.1, Mask: 255.255.0.0, GW: None
Please note that I added a DNS setting for the server.
Then simply create a NAT object on SVRRAS
PS C:> New-NetNat -Name “MyNat1” -InternalIPInterfaceAddressPrefix 172.16.0.0/16
The IP configuration of a VM in the “Private” or “Isolated” subnet should be defined manually like
IP: 172.16.0.31, Mask: 255.255.0.0, GW: 172.16.0.1, DNS: 168.63.129.16
Please note the same external DNS server is used as well.
BTW, this solution could not provide a DHCP server for VMs in the isolated subnet.
In addition to avoiding the installation of Remote Access server role, this solution can support multiple private/isolated subnets as well. For example, if there are two isolated subnets, 172.16.0.0/16 and 172.17.0.0/16, we will need to have three adaptors on the “router” server, SVRRAS; and create two NAT objects: “MyNAT1” and “MyNAT2”
PS C:> New-NetNat -Name “MyNat1” -InternalIPInterfaceAddressPrefix 172.16.0.0/16
PS C:> New-NetNat -Name “MyNat2” -InternalIPInterfaceAddressPrefix 172.17.0.0/16
The solution of using RRSA could also support multiple private/isolated subnets; but it is not easy to configure this using the Routing and Remote Access snap-in.
Saved as a favorite!, I like it!