Save to My DOJO
The virtual switch provided by Hyper-V is compliant with the official 802.1q standard, which means that it can assign its virtual switch ports to virtual local area networks (VLANs). Hyper-V will assign 802.1q VLAN tags to outbound packets from those switch ports and will properly route inbound 802.1q VLAN-tagged packets to their proper virtual switch ports. Understanding the concept is the hardest part; configuring Hyper-V for it is simple.
Thinking in VLANs
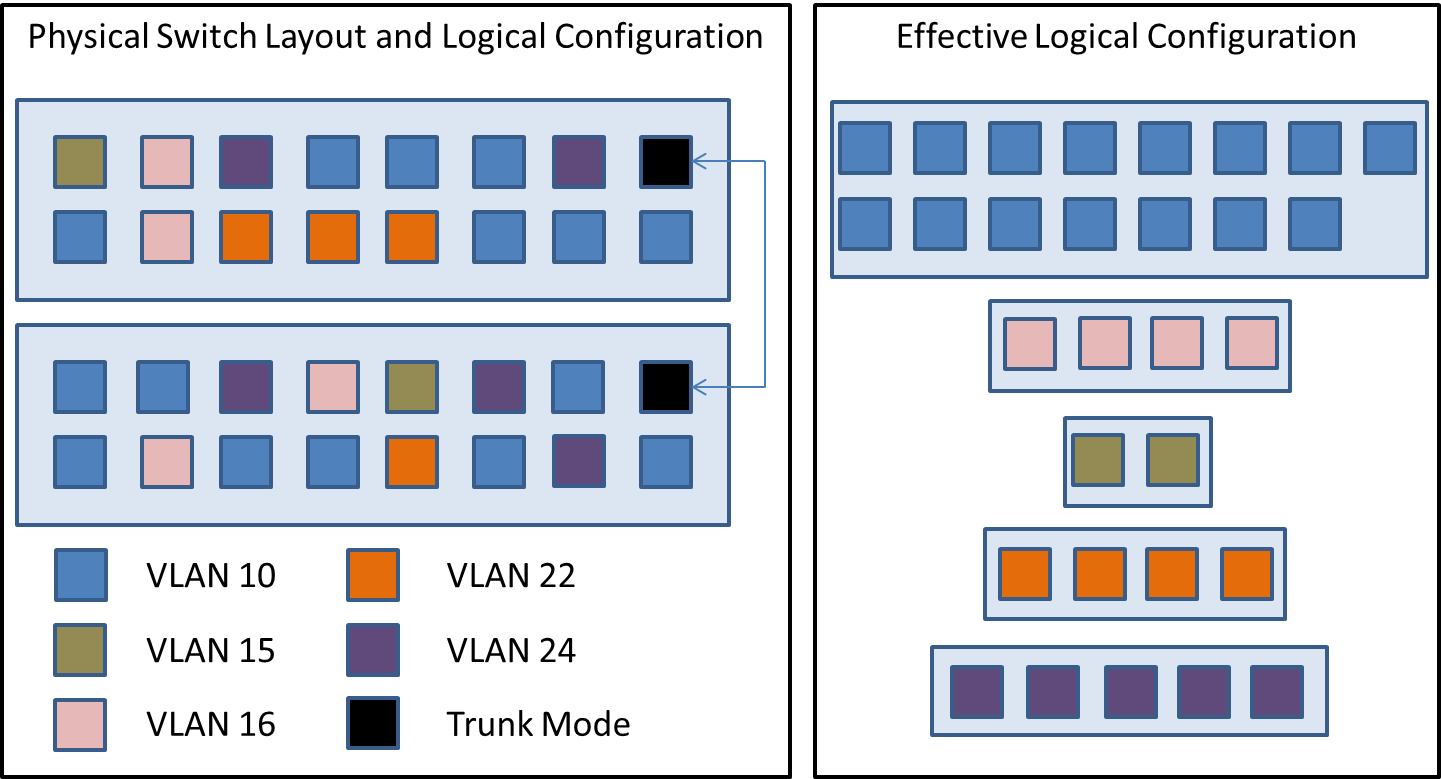
VLAN technology has been around for quite some time but wasn’t common in SMB environments until server virtualization started to catch on. Its primary purpose is to allow physical switch ports to be logically segregated, most commonly for security purposes but also sometimes to reduce the effects of excessive broadcast traffic and other potential congestion-causing problems. Refer to the following diagram:
On the left are two 16-port switches. Their individual ports are configured to be in the VLANs as indicated in the legend. As far as the devices plugged into those switches are concerned, they are configured as seen in the box on the right. Ports connected to a particular VLAN have no direct connectivity to ports in any other VLAN, even if they happen to be on the same physical switch, but they can communicate directly with any other port in the same VLAN, even if it happens to be on another switch – provided that any other physical switches are connected in a trunk.
Hyper-V’s virtual switches have the ability to emulate the above behavior, although it isn’t required. If you do nothing, all traffic traveling across a Hyper-V virtual switch will simply be untagged. If the physical switch that the physical network card you’re using to host your Hyper-V virtual switch doesn’t support 802.1q, then you won’t be able to use this feature. If the physical switch is 802.1q compliant, then you’ll need to set the physical port into trunk mode. For a Cisco IOS switch, this is done with the “switchport mode trunk” command; for other vendors, see the documentation.
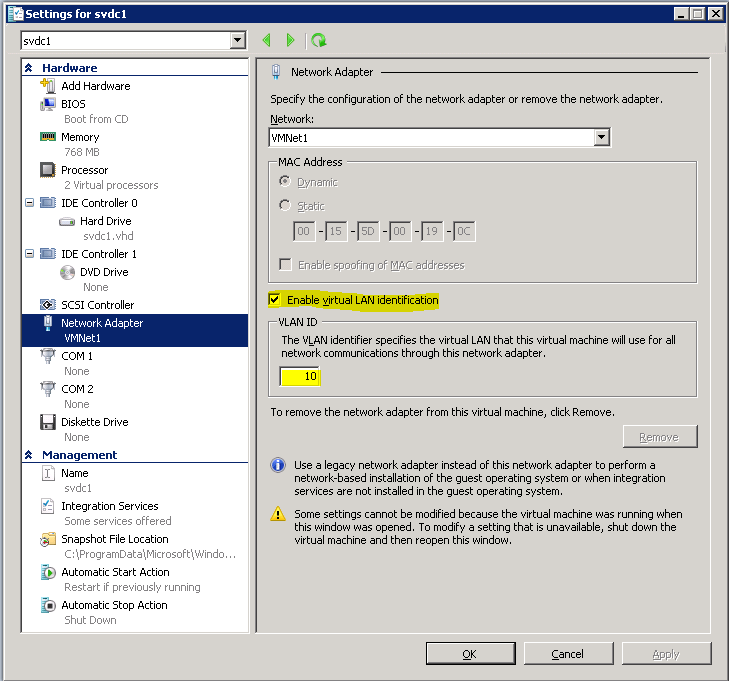
You don’t need to do anything in Hyper-V to enable trunking; it’s on automatically. However, you’ll need to configure individual switch ports for the desired VLAN. To do that, inside Hyper-V Manager, open the settings for the virtual machine you wish to configure. Highlight its virtual network card. The VLAN setting is near the middle of the configuration pane:
Upon clicking OK, all network traffic that this virtual network card sends will be tagged as belonging to VLAN 10. Inbound traffic for this virtual machine must carry 802.1q tags for VLAN 10 or it will be dropped. This virtual network card will receive broadcast traffic traveling on VLAN 10.
VLAN for the Physical NIC
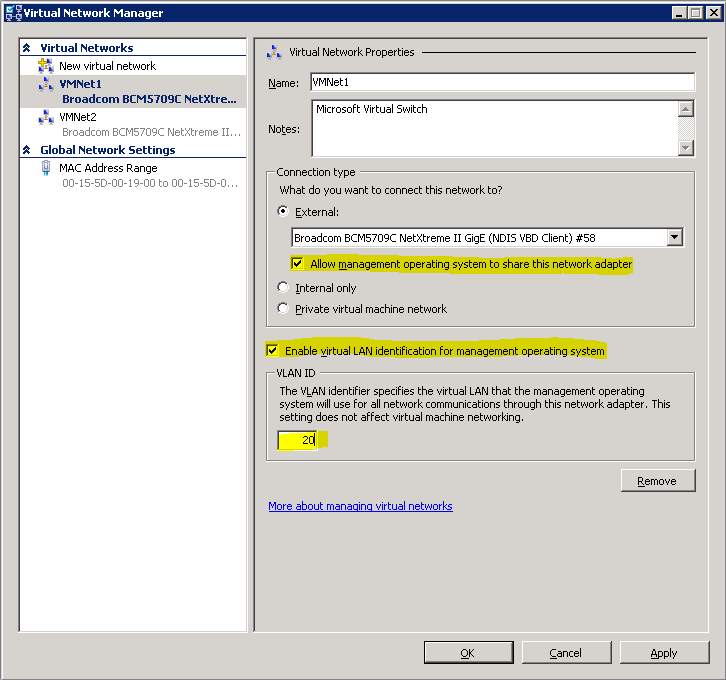
In the properties box for the virtual switch, it is possible to connect the management operating system to a VLAN as well, if you’ve allowed it to share the physical adapter. “Sharing” is misleading here. What actually happens is that Hyper-V creates a virtual switch port for the management operating system and connects it to the virtual switch. The management operating system’s adapter won’t behave any differently than a virtual machine’s would:
What About the Native VLAN?
If you know much about Cisco configurations, then you know that it’s possible to set a native VLAN on trunked ports. For other manufacturers, this is called the port VLAN identifier (PVID). Basically, this tells the switch port which VLAN it should consider untagged packets to be a part of. There is no equivalent to this in Hyper-V networking. The reason is because this is a port setting. Since Hyper-V switches are virtual and there isn’t actually a port being used for the trunk, the idea of a native VLAN/PVID really has no meaning. If the virtual switch receives untagged packets, it will distribute them to virtual switch ports that haven’t been assigned a VLAN. When those ports send their traffic, it will go out untagged and land on other untagged virtual switch ports and up the physical wire where the connected switch’s PVID/native VLAN will handle them.
VLAN Troubleshooting
Fortunately, there isn’t much that can go wrong here. If VLAN traffic isn’t traveling as expected, there are only three places to check.
The Physical Switch
First, the physical switch has to support 802.1q trunking and the port that the Hyper-V physical NIC is connected to must be in trunk mode. Some switches also have security options that allow/disallow particular VLANs to participate in trunks. For a Cisco switch, the place to start is with the “show interface trunk” command. Other manufacturers will have similar options.
System Center Virtual Machine Manager
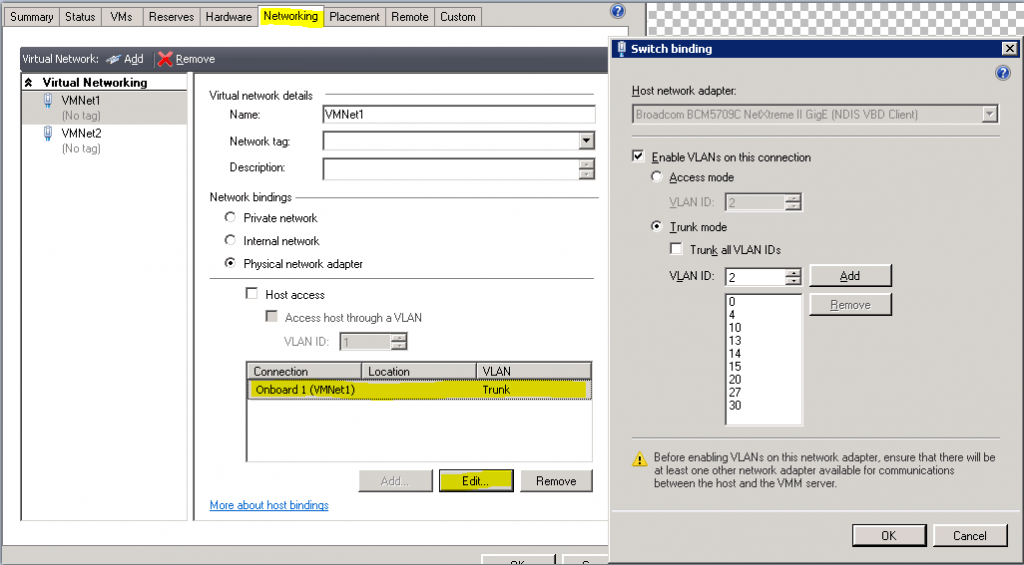
It’s possible for SCVMM to exercise tighter control over virtual switches than can be done with Hyper-V Manager. It can restrict VLAN traffic much the way that Cisco switches do. To check its settings, open the properties of the host computer. Switch to the networking tab. Highlight the virtual network on the left. On the right pane near the bottom, under “Connection”, highlight the physical network adapter (its VLAN will be “Trunk”). Click the “Edit…” button and you will be presented with the dialog box as seen below. If you do not elect to trunk all VLANs, you’ll need to manually enter those that you do wish to allow. If you change the dot to “Access mode”, then all virtual switch ports that aren’t tagged will be transmitted to each other and the physical network on VLAN 2; other virtual switch port traffic will be dropped.
Settings Inside the Virtual Machine
If your physical and virtual switches are configured properly and you’re still having trouble, the final place to check is the virtual machine itself. You’ll troubleshoot this the same way that you would for a physical computer. Make sure that it recognizes the network adapter and has loaded a driver for it. If it does, then ensure its TCP/IP settings are correct. Occasionally, the VLAN setting in Hyper-V doesn’t “stick” or the virtual machine doesn’t recognize it right away. In these cases, you can re-apply the setting first. If that doesn’t work, try shutting down the virtual machine and starting it back up. If your host is part of a cluster, sometimes LiveMigrating the virtual machine from one host to another gets the VLAN setting to “wake up”.
Have any questions?
Leave a comment below!
Backing up Hyper-V
If you’d like to make backing up your Hyper-V VMs easy, fast and reliable, check out Altaro Hyper-V Backup v4. It’s free for up to 2 VMs and supports Hyper-V Server 2012 R2! Need more? Download a 30-day trial of our Unlimited Edition here: http://www.altaro.com/hyper-v-backup/.


Not a DOJO Member yet?
Join thousands of other IT pros and receive a weekly roundup email with the latest content & updates!










17 thoughts on "VLAN Trunking for Hyper-V Guests"
I have make a trunk adaptor to a vm.
How can I set ip adresses on de differend Vlans in the VM ?
I have 12 VLAN’s dat must communicate to that VM.
That’s not how trunk adapters work in a virtual machine. You need software inside it that can decode the 802.1q tag of an Ethernet frame. Otherwise, if you need a VM to participate in 12 VLANs, then it needs 12 adapters, one per VLAN, and an IP for each.
I am running several VMs on win8.1 host. I noticed very high disk activity on the virtual c drive of 2 of my win8.1 guests. But only when they are running at the same time. Disable the virtual NIC, and disk activity drops from 100% to 0%, or normal if you will. Could this issue be helped by using Vlan? Is it possible to do with a r6300 router?
That’s highly unusual behavior. No, I don’t expect trunking to help. Use procmon or something to see what’s going on.
Eric
Thanks for the great Info.
Is it possible to make VM network adapter as trunk port so that Guest OS will send and receive tagged packet?
Till now what i understand that Network adapter on VM can has only one VLAN ID, if you want multiple VLANs in that case we have to create multiple network adapter.
Yes, you can set a virtual adapter in trunk mode, but you’ll need software inside the virtual machine that can handle tagged traffic. Windows will not do it alone. For most purposes, you will need multiple virtual adapters.
I have a VM with an interface that can handle VLAN tagged traffic. What is the configuration on the virtual adapter for this VM to ensure traffic is flowing to it with all packets tagged to their respective VLANs?
Not sure what you’re asking. If it’s configured, then it’s flowing. You need something that can intercept the layer 2 frames if you need to see what’s happening.
Hi Eric, may I know the software which can set a virtual adapter in trunk mode and tell us if that’s a open source or closed source.
Hyper-V’s built-in PowerShell cmdlets set the trunk mode. No, it’s not open source.
Great article.
I am implementing a PaloAlto VM firewall, in which I am trying to configure subinterfaces with VLANs. Since in this configuration the Palo is a VM itself, I won’t be utilizing Hyper-V external switches but instead a Hyper-V private switch. I have two VMs set up with VLAN identification (3 & 4), connected to a private switch that is also connected to the Palo VM.
For whatever reason, I can’t even ping between the VMs. I am still trying to wrap my head around this. Do you know if the Hyper-V private switch support VLAN tagged traffic?
Any thoughts would be appreciated.
Internal/external/private virtual switches only differ by host involvement and physical NIC usage. VLAN functionality does not change. But you did put the VMs on the same private switch, right? And have ensured standard IP connectivity across them?
Boa noite pessoal. tenho um problema e gostaria de ajuda vossa.
tenho uma maquina que tem apenas duas placas de rede física. criei 5 maquinas virtuais no Hyper-V, queria que numa porta física saísse três redes deferente. por exemplo 172. 31. 40.0 , 172.31.20.0 e 172.31.10.0.
alguém me ajuda por favor.